Which Of These Protocols Use Asymmetric Key Algorithms To Live By
Which Of These Protocols Use Asymmetric Key Algorithms To Live By - Keeping kids occupied can be challenging, especially on busy days. Having a bundle of printable worksheets on hand makes it easier to encourage learning without much planning or screen time.
Explore a Variety of Which Of These Protocols Use Asymmetric Key Algorithms To Live By
Whether you're supplementing schoolwork or just want an educational diversion, free printable worksheets are a great tool. They cover everything from numbers and spelling to puzzles and creative tasks for all ages.

Which Of These Protocols Use Asymmetric Key Algorithms To Live By
Most worksheets are quick to print and use right away. You don’t need any special supplies—just a printer and a few minutes to set things up. It’s convenient, quick, and effective.
With new themes added all the time, you can always find something fresh to try. Just download your favorite worksheets and turn learning into fun without the hassle.

Difference Between Symmetric Key Cryptography And Asymmetric Key
:max_bytes(150000):strip_icc()/algorithm-df9b57e8ea7c494b891da25987643fab.jpg)
Algorit What An Algorithm Is And Implications For Trading Miglobo mx
Which Of These Protocols Use Asymmetric Key Algorithms To Live By
Gallery for Which Of These Protocols Use Asymmetric Key Algorithms To Live By
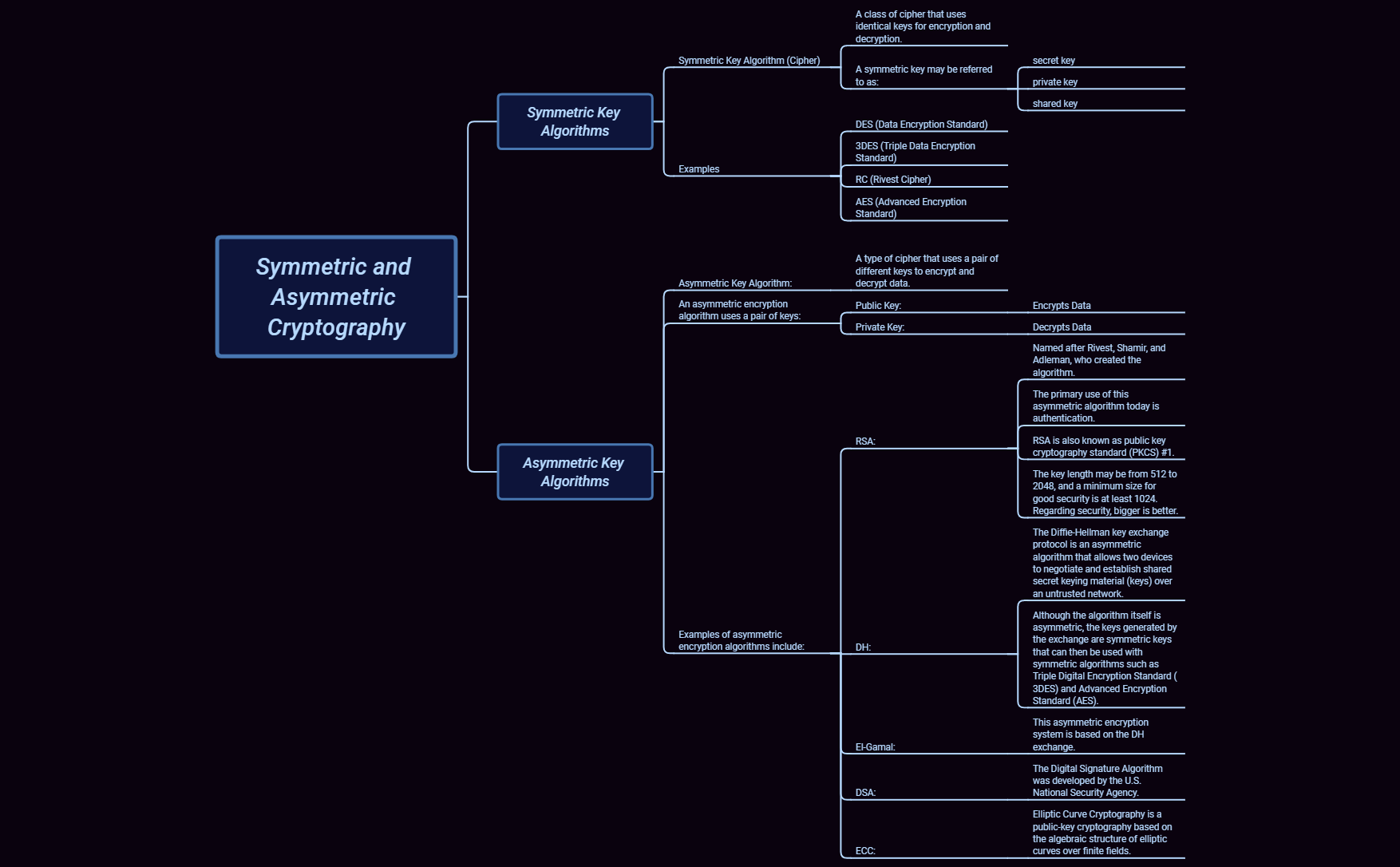
6 1 2 Symmetric And Asymmetric Cryptography XMind Mind Mapping Software

Beginners Guide To Cryptography Quick

2 Advantage And Weakness In Asymmetric Algorithms Download Table
Cryptography

Http Https
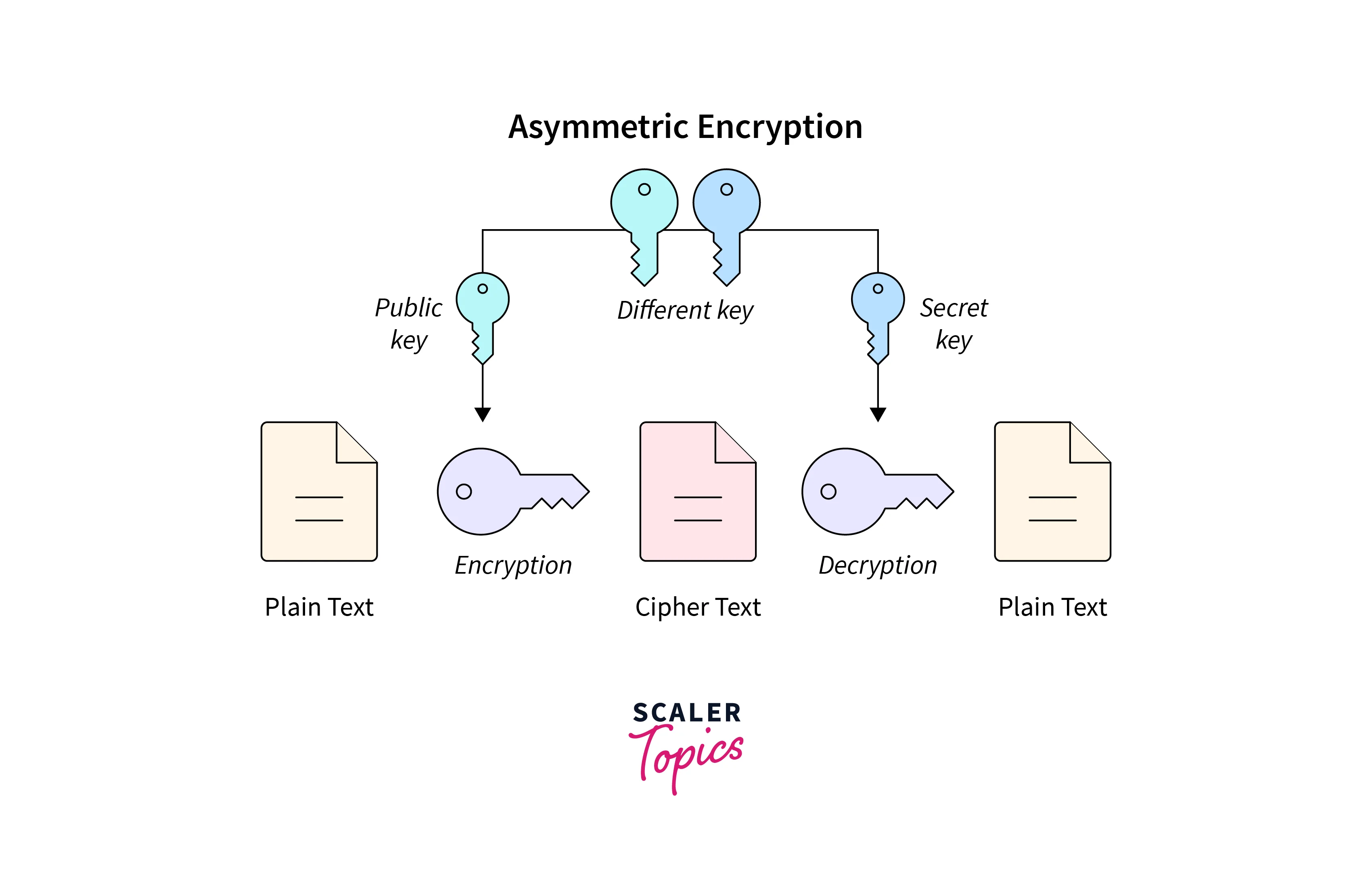
Difference Between Symmetric And Asymmetric Key Encryption Scaler Topics
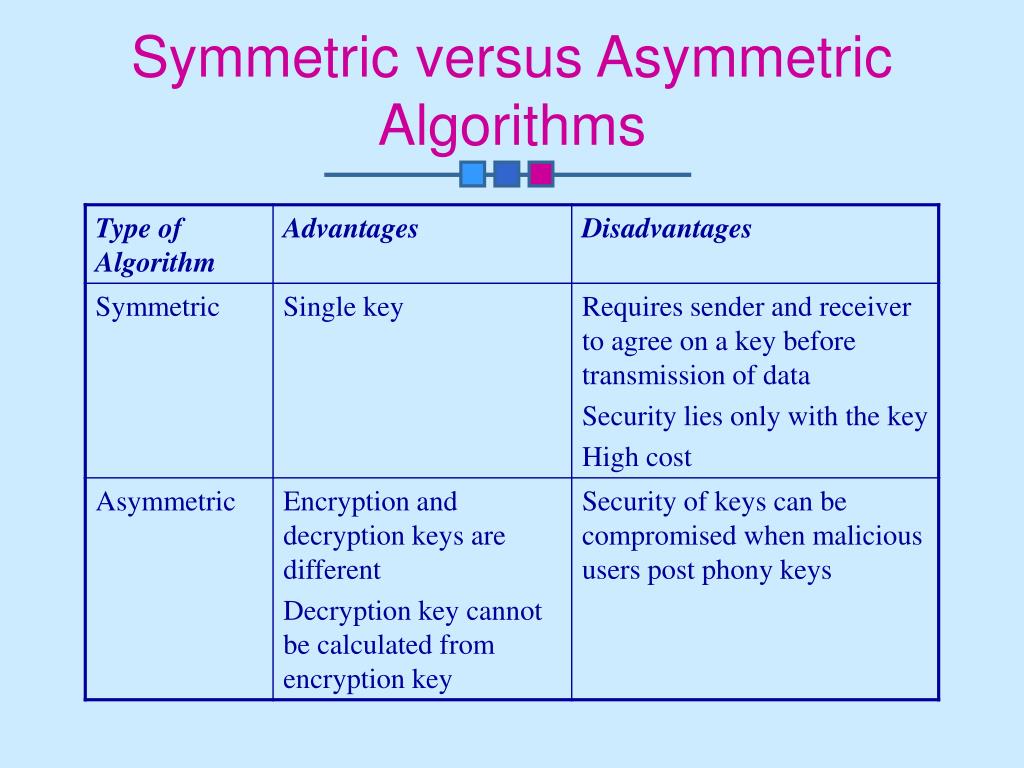
PPT Cryptography PowerPoint Presentation Free Download ID 2976726
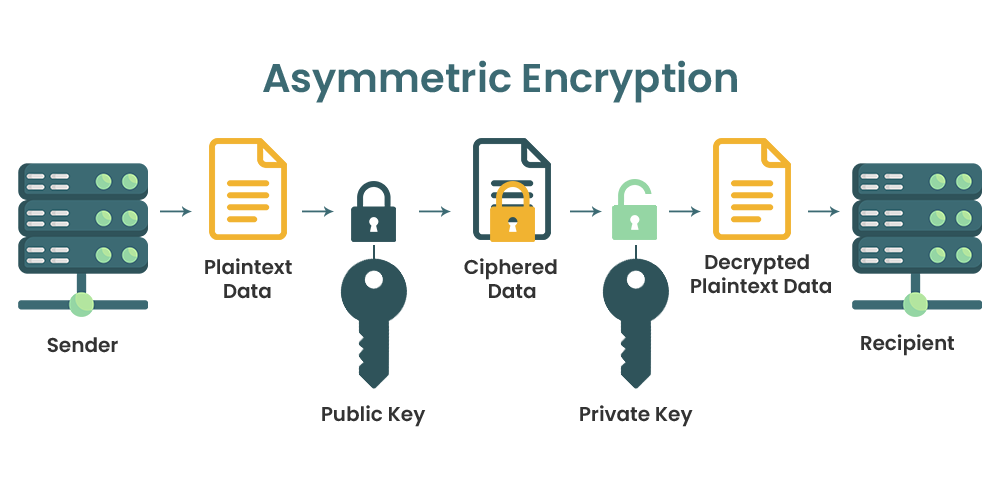
Asymmetric Encryption Penetration Testing And CyberSecurity Solution
Public Key Cryptography Algorithms

Cryptography An Introduction Continued Ppt Download