Which Of These Protocols Use Asymmetric Key Algorithms
Which Of These Protocols Use Asymmetric Key Algorithms - Keeping kids occupied can be challenging, especially on hectic schedules. Having a bundle of printable worksheets on hand makes it easier to provide educational fun without extra prep or electronics.
Explore a Variety of Which Of These Protocols Use Asymmetric Key Algorithms
Whether you're helping with homework or just want an educational diversion, free printable worksheets are a great tool. They cover everything from math and spelling to games and creative tasks for all ages.

Which Of These Protocols Use Asymmetric Key Algorithms
Most worksheets are quick to print and use right away. You don’t need any fancy tools—just a printer and a few minutes to get started. It’s simple, quick, and practical.
With new themes added all the time, you can always find something exciting to try. Just download your favorite worksheets and turn learning into fun without the hassle.

Difference Between Symmetric Asymmetric Key Cryptography Symmetric

Difference Between Symmetric Key Cryptography And Asymmetric Key
Which Of These Protocols Use Asymmetric Key Algorithms
Gallery for Which Of These Protocols Use Asymmetric Key Algorithms
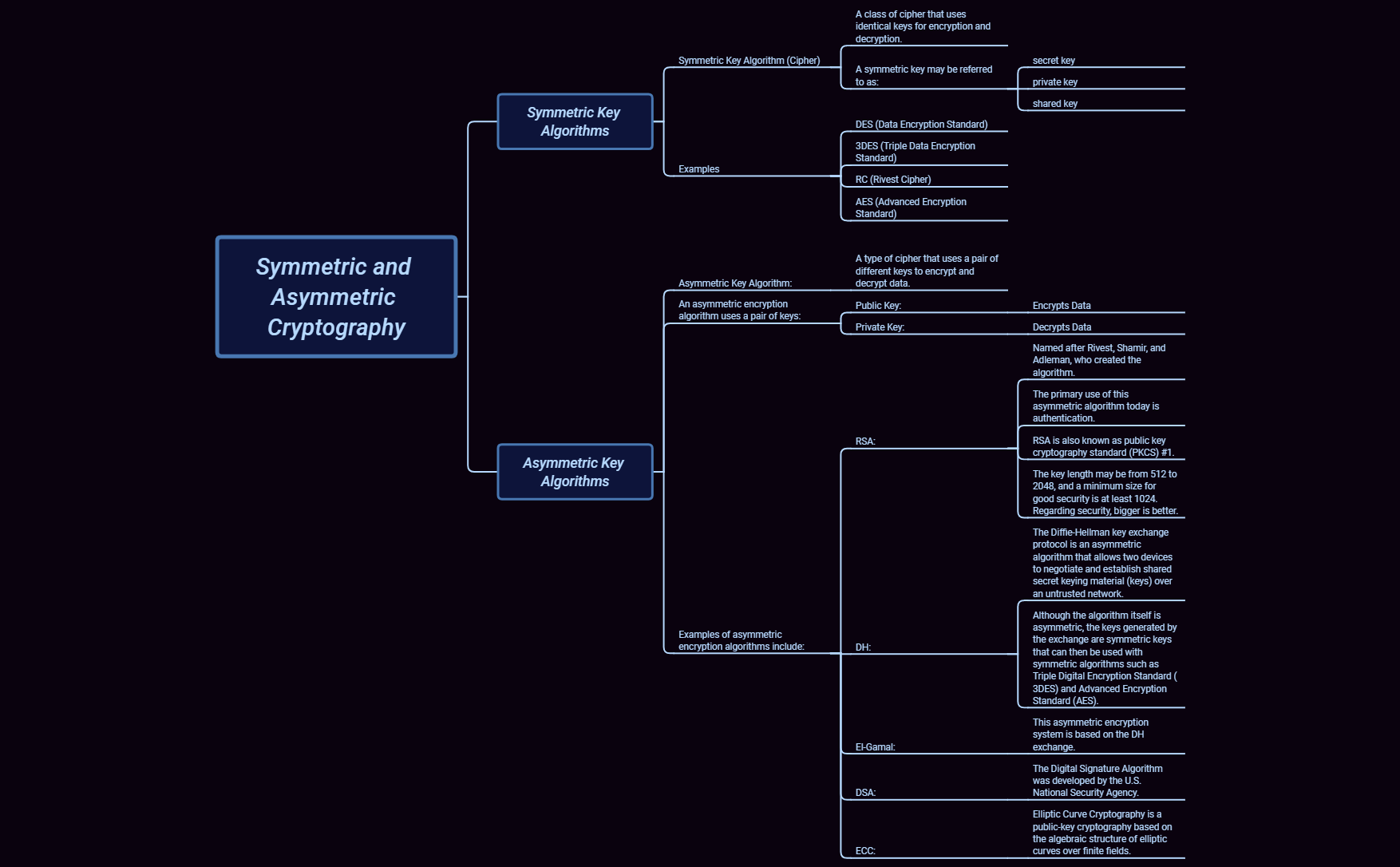
6 1 2 Symmetric And Asymmetric Cryptography XMind Mind Mapping Software
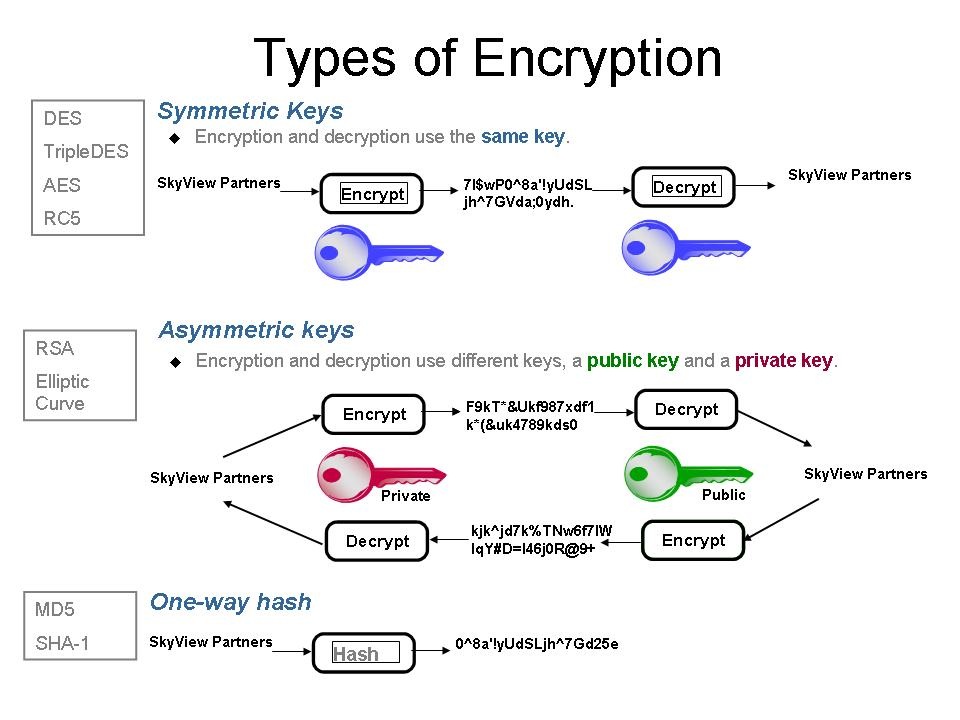
Encryption Internet Security

Beginners Guide To Cryptography Quick

2 Advantage And Weakness In Asymmetric Algorithms Download Table
Cryptography

Http Https
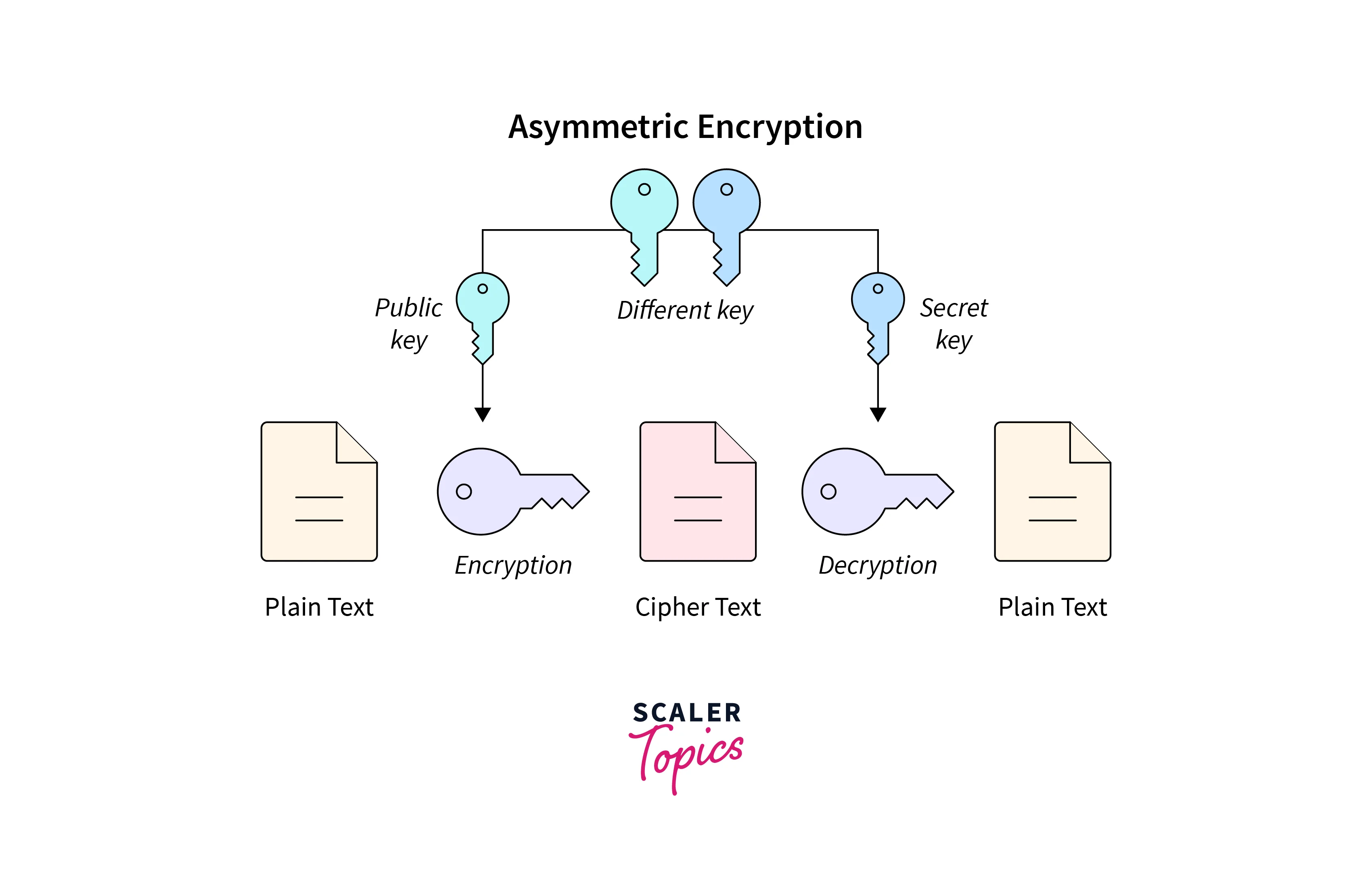
Difference Between Symmetric And Asymmetric Key Encryption Scaler Topics
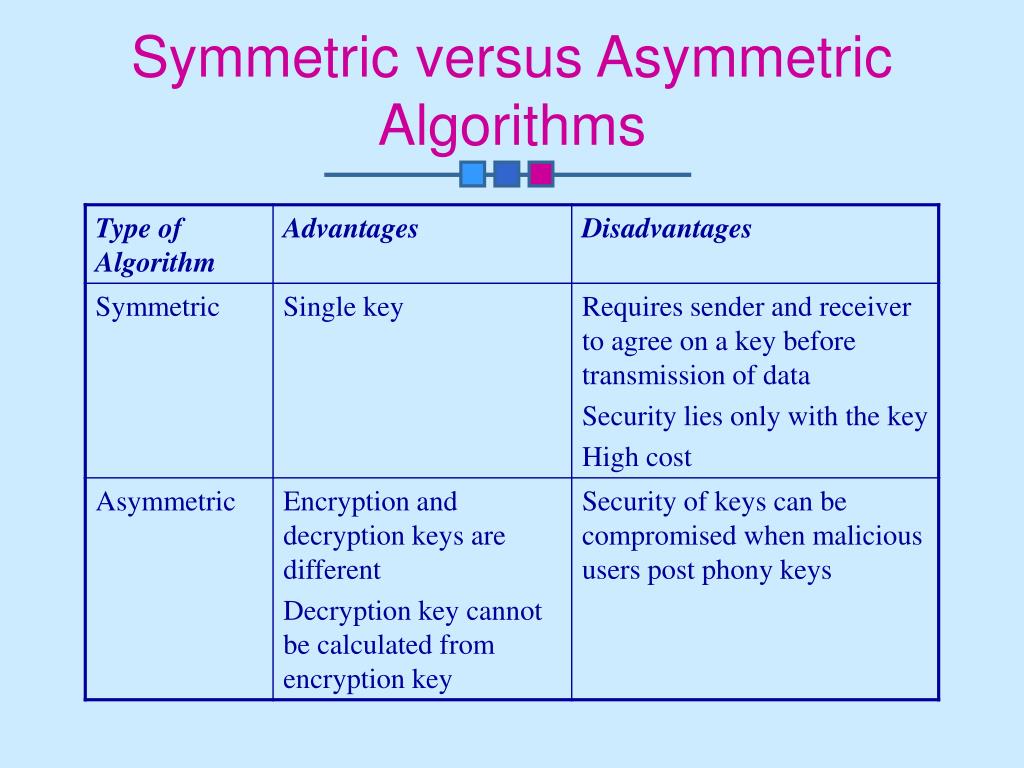
PPT Cryptography PowerPoint Presentation Free Download ID 2976726

Working Of The Asymmetric Key Algorithm Download Scientific Diagram
Public Key Cryptography Algorithms