Which Of The Following Are Examples Of Vulnerabilities Exploited By Our
Which Of The Following Are Examples Of Vulnerabilities Exploited By Our - Keeping kids engaged can be challenging, especially on hectic schedules. Having a bundle of printable worksheets on hand makes it easier to encourage learning without much planning or electronics.
Explore a Variety of Which Of The Following Are Examples Of Vulnerabilities Exploited By Our
Whether you're doing a quick lesson or just want an educational diversion, free printable worksheets are a helpful resource. They cover everything from math and spelling to puzzles and coloring pages for all ages.

Which Of The Following Are Examples Of Vulnerabilities Exploited By Our
Most worksheets are easy to access and use right away. You don’t need any special supplies—just a printer and a few minutes to get started. It’s simple, fast, and practical.
With new themes added all the time, you can always find something exciting to try. Just grab your favorite worksheets and make learning enjoyable without the stress.

How To Find Vulnerabilities And Exploits YouTube

Brawl Vault
Which Of The Following Are Examples Of Vulnerabilities Exploited By Our
Gallery for Which Of The Following Are Examples Of Vulnerabilities Exploited By Our

Security Assessments Ferraris Investigations Consulting LLC

Vulnerability Scanning WebCheck Security
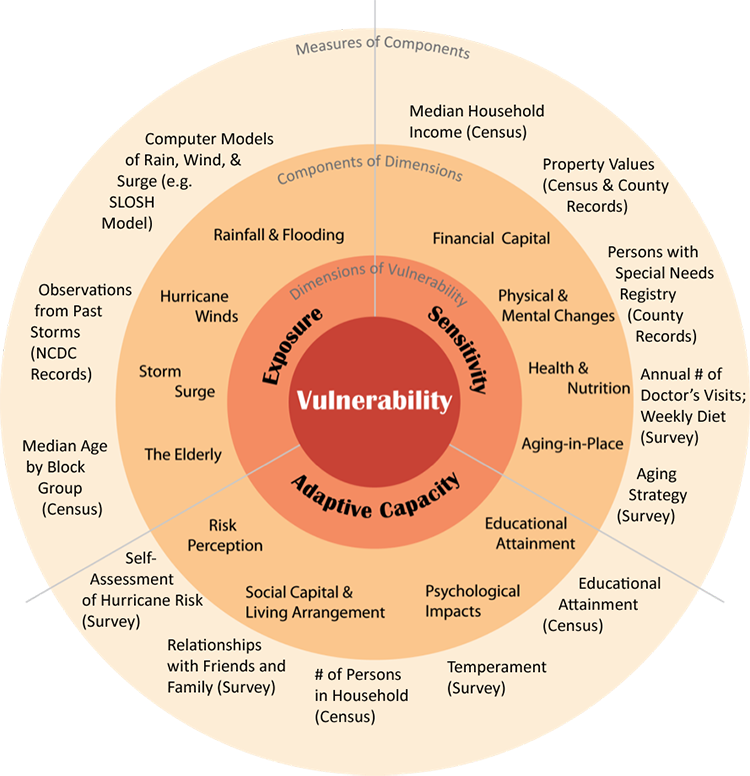
Assessing Vulnerability The Vulnerability Scoping Diagram Coastal

Objective
Vulnerable

Vulnerability Lanworks
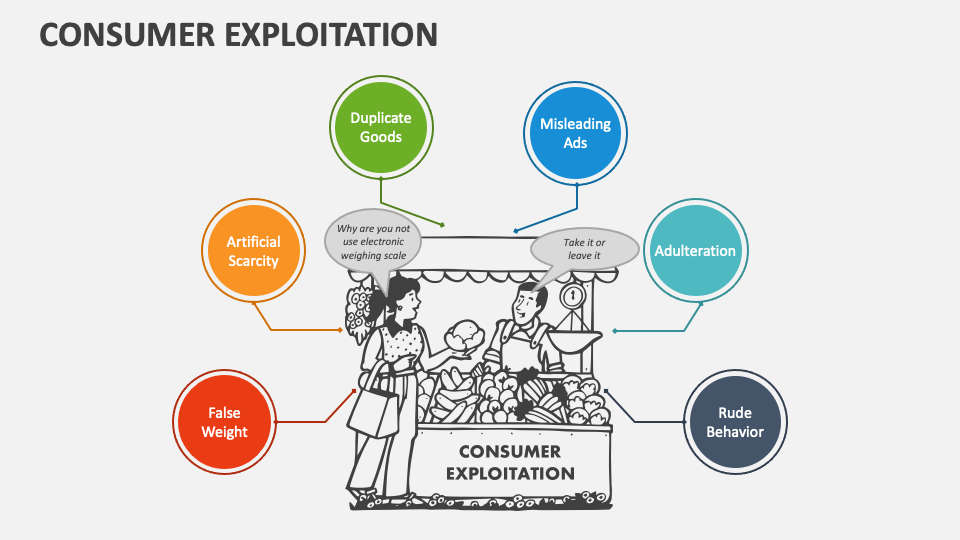
Consumer Exploitation PowerPoint And Google Slides Template PPT Slides

Which Of The Following Are Examples Of Irrational Numbers Select All

Vulnerability Disaster Management

Top Vulnerability Scanners Kidslopte