What Are Examples Of Vulnerabilities Exploited By Our Adversaries To Collect Your Information
What Are Examples Of Vulnerabilities Exploited By Our Adversaries To Collect Your Information - Keeping kids occupied can be challenging, especially on busy days. Having a collection of printable worksheets on hand makes it easier to encourage learning without extra prep or screen time.
Explore a Variety of What Are Examples Of Vulnerabilities Exploited By Our Adversaries To Collect Your Information
Whether you're supplementing schoolwork or just want an activity break, free printable worksheets are a great tool. They cover everything from numbers and spelling to puzzles and creative tasks for all ages.
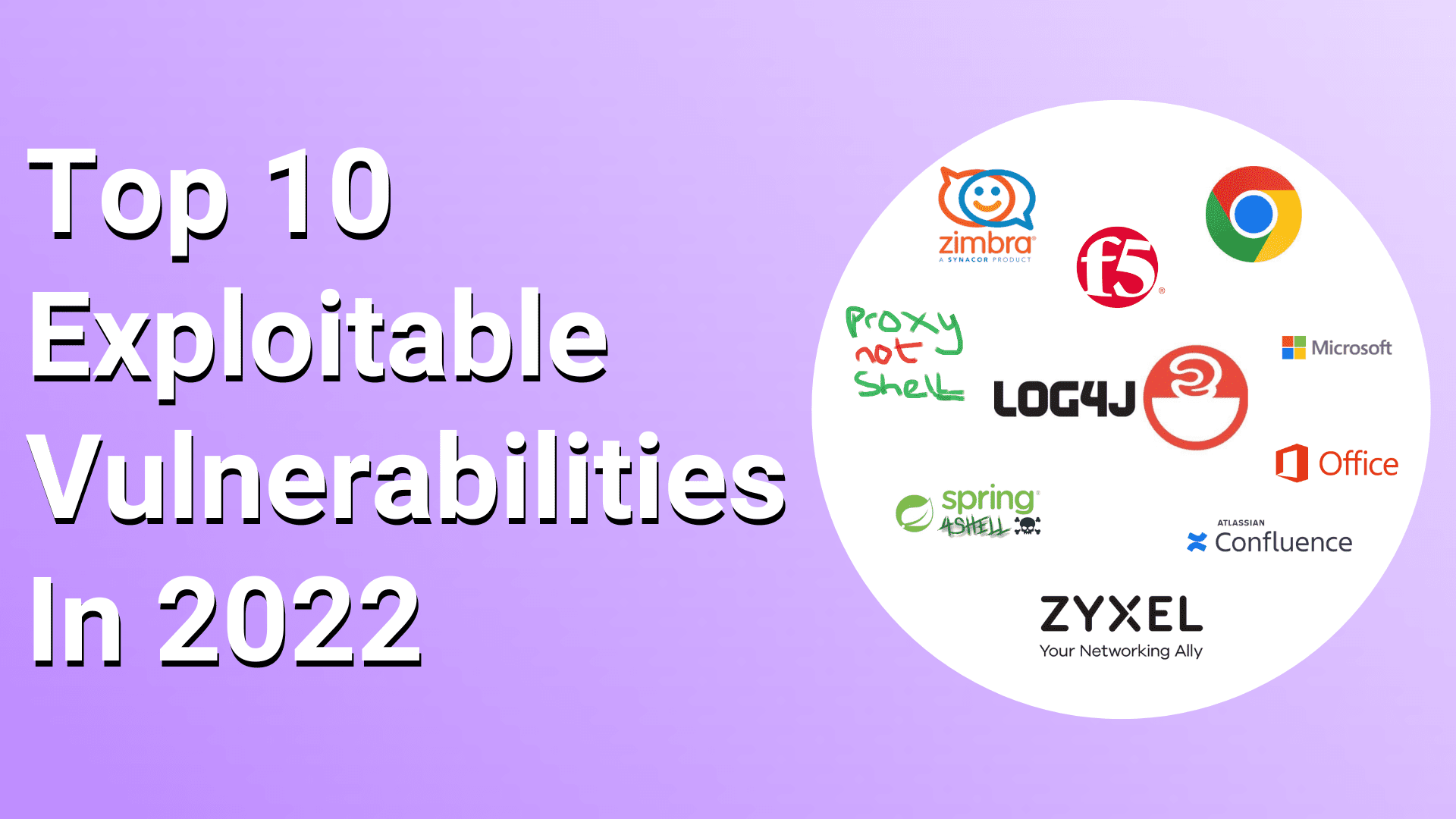
What Are Examples Of Vulnerabilities Exploited By Our Adversaries To Collect Your Information
Most worksheets are easy to access and ready to go. You don’t need any fancy tools—just a printer and a few minutes to set things up. It’s convenient, quick, and effective.
With new themes added all the time, you can always find something exciting to try. Just download your favorite worksheets and make learning enjoyable without the hassle.

Vulnerabilities In IoT YouTube

How To Find Vulnerabilities And Exploits YouTube
What Are Examples Of Vulnerabilities Exploited By Our Adversaries To Collect Your Information
Gallery for What Are Examples Of Vulnerabilities Exploited By Our Adversaries To Collect Your Information
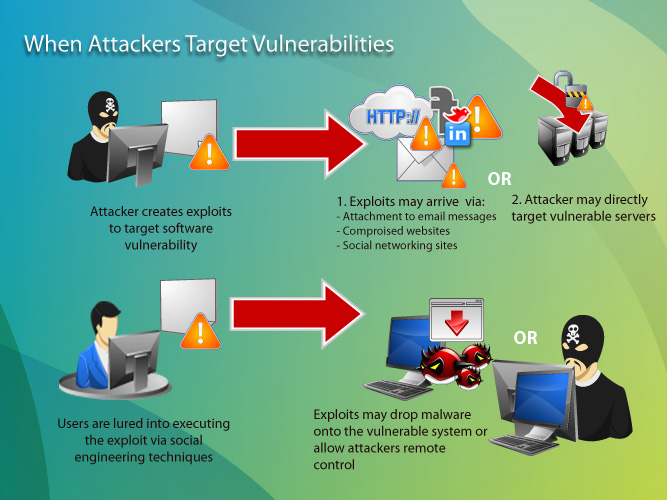
Exploit Word

Application vulnerability exploits RMS Tech

Vulnerability Scanning WebCheck Security

Software Vulnerability FineProxy Glossary
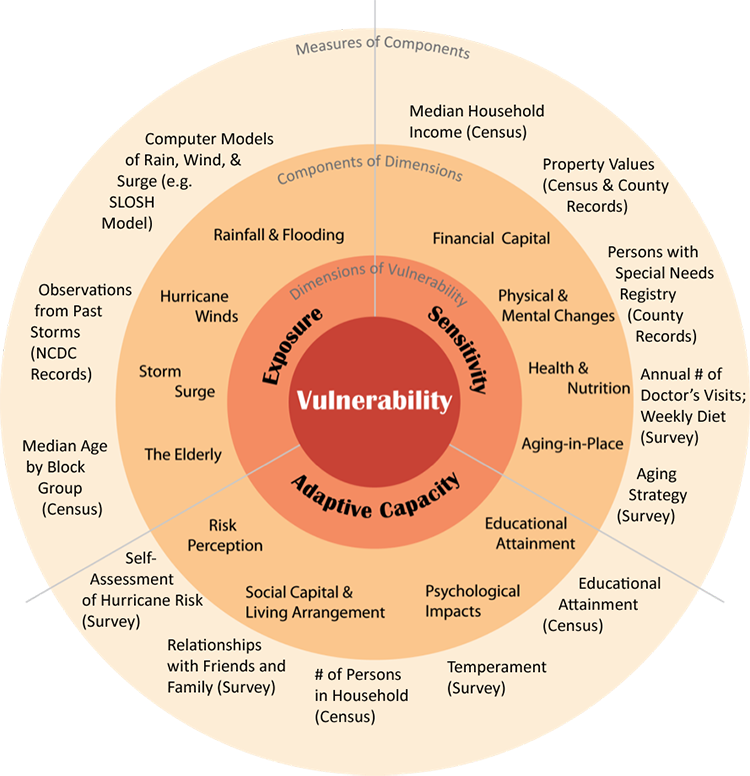
Assessing Vulnerability The Vulnerability Scoping Diagram Coastal

Integrated Vector Management Program Engage San Diego County

Vulnerability Lanworks
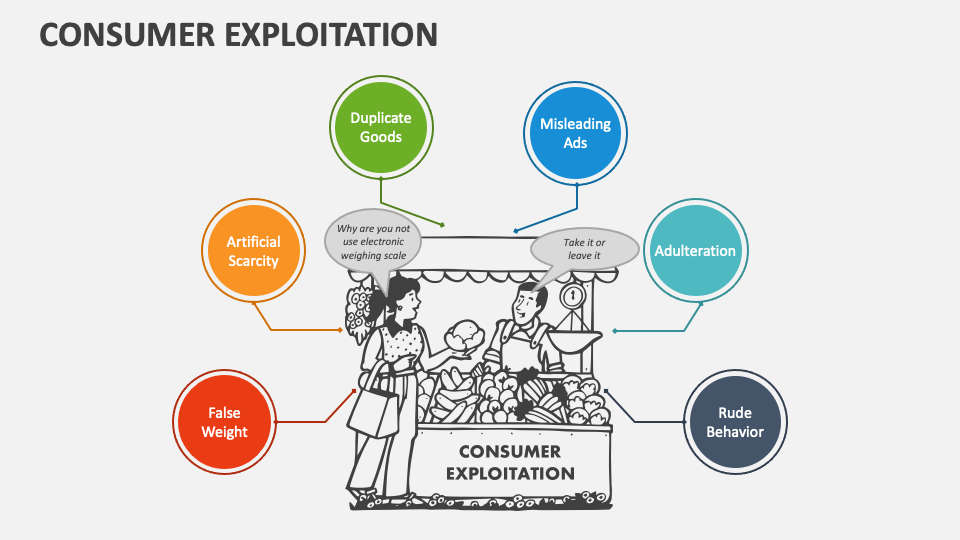
Consumer Exploitation PowerPoint And Google Slides Template PPT Slides

Information Theft

Turm Das Internet Sicherung Monitor Iot Device Oper Abwesenheit Schaffung