Ssh Weak Mac Algorithms Enabled Nmap
Ssh Weak Mac Algorithms Enabled Nmap - Keeping kids engaged can be tough, especially on busy days. Having a bundle of printable worksheets on hand makes it easier to encourage learning without extra prep or screen time.
Explore a Variety of Ssh Weak Mac Algorithms Enabled Nmap
Whether you're doing a quick lesson or just want an educational diversion, free printable worksheets are a great tool. They cover everything from math and spelling to games and creative tasks for all ages.
Ssh Weak Mac Algorithms Enabled Nmap
Most worksheets are quick to print and use right away. You don’t need any fancy tools—just a printer and a few minutes to set things up. It’s convenient, fast, and practical.
With new themes added all the time, you can always find something fresh to try. Just download your favorite worksheets and make learning enjoyable without the stress.
12 hash And MAC Algorithms PDF Military Communications Security
Jul 18 2009 nbsp 0183 32 Generate a SSH key if you don t have one If you happen to use GNOME the seahorse application quot Passwords and Encryption Keys quot can do it for you File gt New gt Oct 16, 2014 · Ssh offers two kinds of keep-alives: TCP keep-alives and ssh keep-alives. TCP does offer a mechanism to automatically close connections deemed dead because of timeout. …
Removing SSH Weak Ciphers SDWAN Router Controller Mode Cisco Community
Ssh Weak Mac Algorithms Enabled NmapWith ssh -i <private key filename> you can instruct ssh to use an extra private key to try authentication. The documentation is not clear on how to explicitly use only that key. Apr 1 2020 nbsp 0183 32 How do I set the host name and port in a config file for Windows using OpenSSH through PowerShell As on Unix Linux Edit or create the file now by typing nano ssh config
Gallery for Ssh Weak Mac Algorithms Enabled Nmap

SSL TLS Security Testing SSL TLS Weak Cipher Security Testing Using

TLS Essentials 3 Confidentiality With AES RSA Hybrid Encryption

SSH Vulnerabilities MAC Algorithms And CBC Ciphers Resolved Tech

SSH Vulnerabilities MAC Algorithms And CBC Ciphers Disable Weak
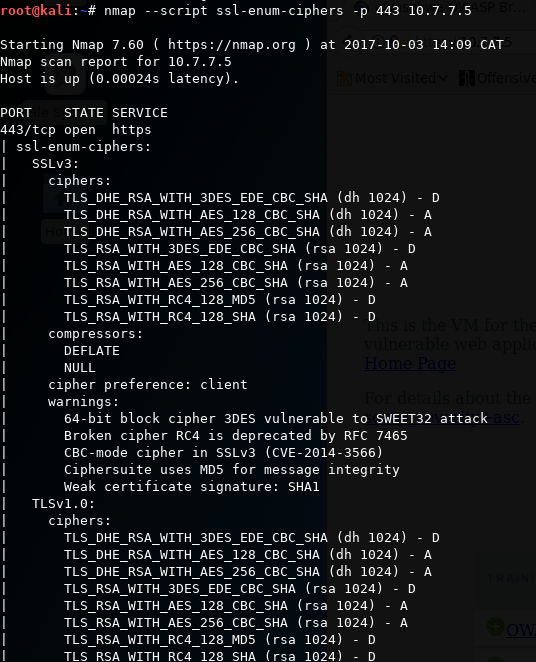
Tls Linux
Rebooting A HPE Aruba 5400R Zl2 With Dual Management Modules Following
List Of SSH Weak MAC Is Hmac sha2 256 And Hmac sha2 512 50 OFF
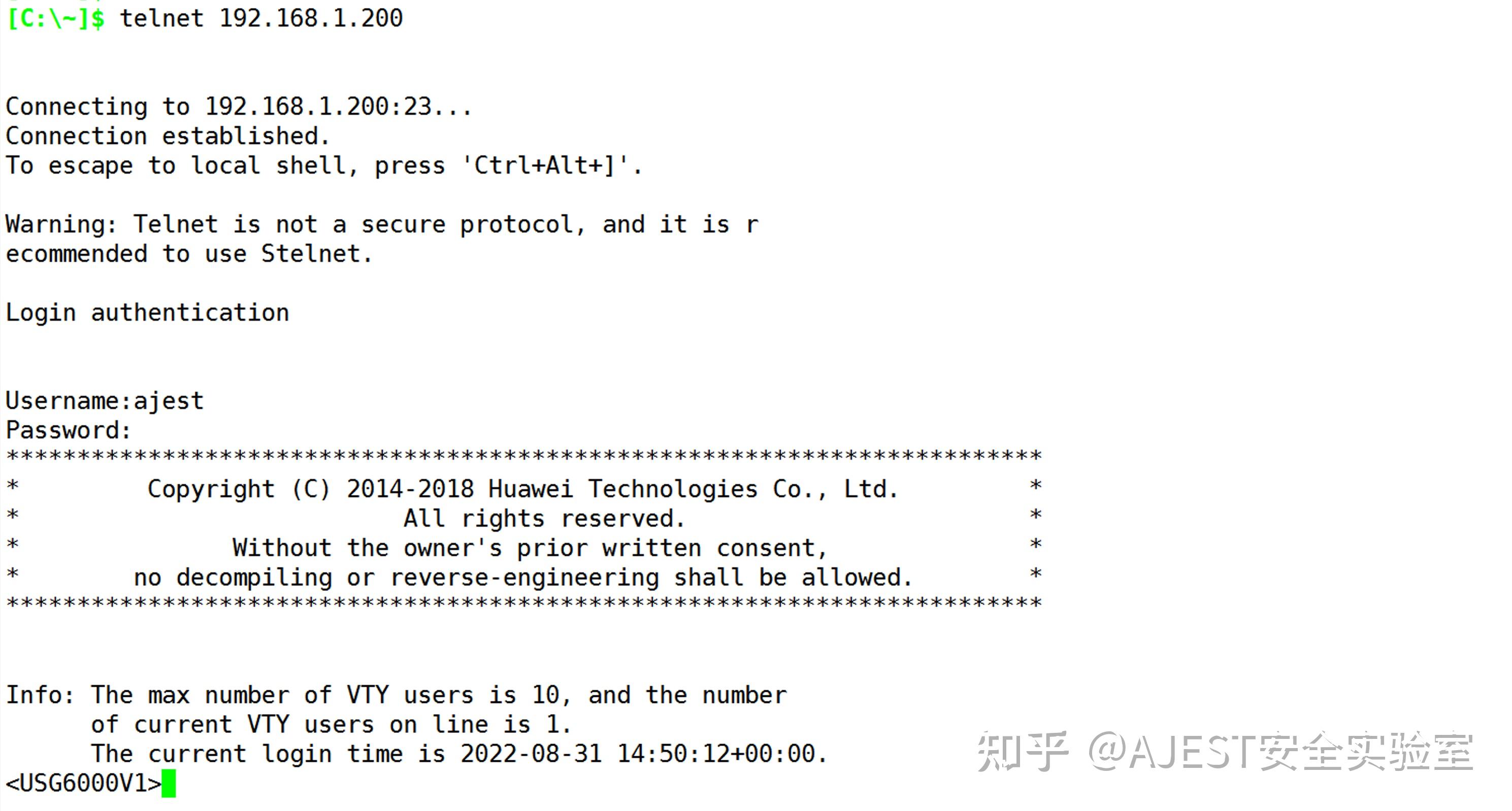
USG6000

SSH Weak Key Exchange Algorithms Enabled Tenable

SSH Weak Key Exchange Algorithms Enabled Tenable



