Ssh Encryption Algorithms
Ssh Encryption Algorithms - Keeping kids occupied can be challenging, especially on hectic schedules. Having a bundle of printable worksheets on hand makes it easier to keep them learning without much planning or electronics.
Explore a Variety of Ssh Encryption Algorithms
Whether you're supplementing schoolwork or just want an activity break, free printable worksheets are a great tool. They cover everything from numbers and spelling to puzzles and coloring pages for all ages.
Ssh Encryption Algorithms
Most worksheets are easy to access and ready to go. You don’t need any special supplies—just a printer and a few minutes to get started. It’s simple, fast, and effective.
With new themes added all the time, you can always find something fresh to try. Just grab your favorite worksheets and make learning enjoyable without the stress.
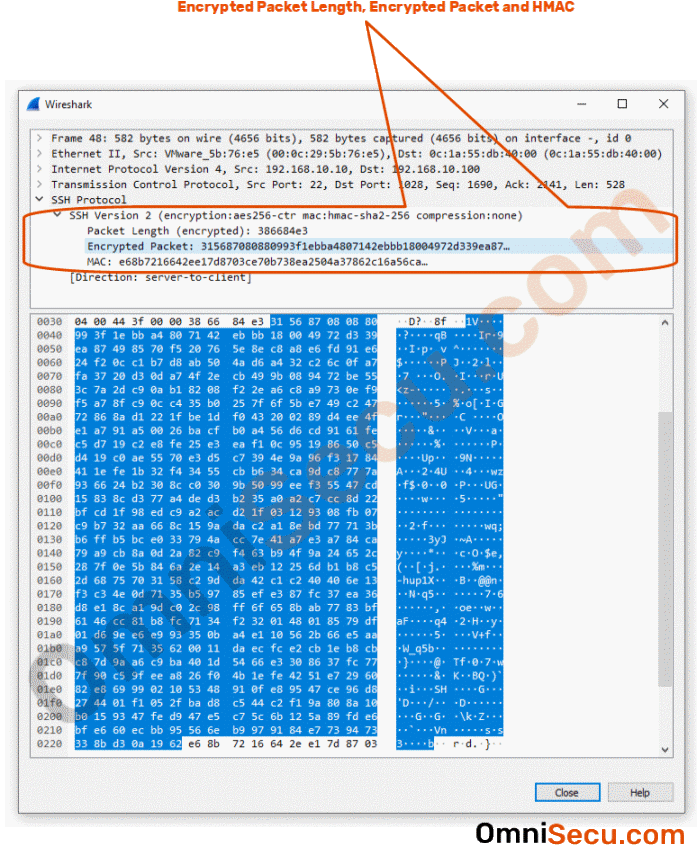
SSH Packet Format
Jul 18 2009 nbsp 0183 32 Generate a SSH key if you don t have one If you happen to use GNOME the seahorse application quot Passwords and Encryption Keys quot can do it for you File gt New gt Oct 16, 2014 · Ssh offers two kinds of keep-alives: TCP keep-alives and ssh keep-alives. TCP does offer a mechanism to automatically close connections deemed dead because of timeout. …

Or Call For Office Visit Ppt Download
Ssh Encryption AlgorithmsWith ssh -i <private key filename> you can instruct ssh to use an extra private key to try authentication. The documentation is not clear on how to explicitly use only that key. Apr 1 2020 nbsp 0183 32 How do I set the host name and port in a config file for Windows using OpenSSH through PowerShell As on Unix Linux Edit or create the file now by typing nano ssh config
Gallery for Ssh Encryption Algorithms
Jayreka Blog

Secure Shell

Unix System Administration Ppt Download

Technical Issues In Web And Mobile Apps Ppt Download

SSH Key Algorithms RSA Vs ECDSA Vs Ed25519 VulnerX
SSH Key Algorithms RSA Vs ECDSA Vs Ed25519 VulnerX
PHP Encryption Guide To Top 3 Types Of PHP Encryption In Detail
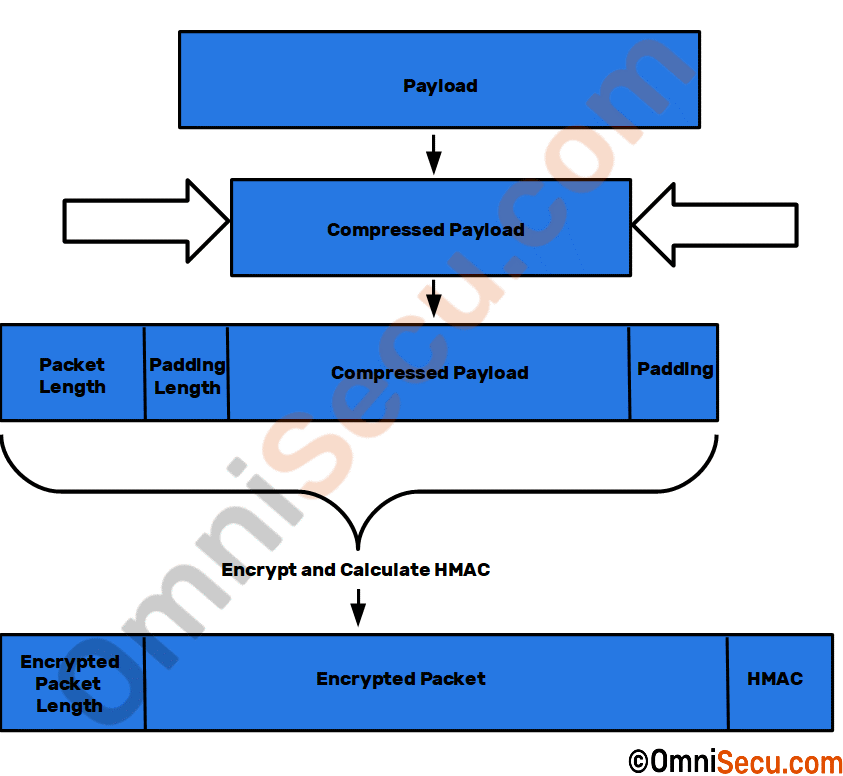
How SSH Works

IFIP UNU ADVANCED COURSE ON NETWORKING AND SECURITY Module II Wireless
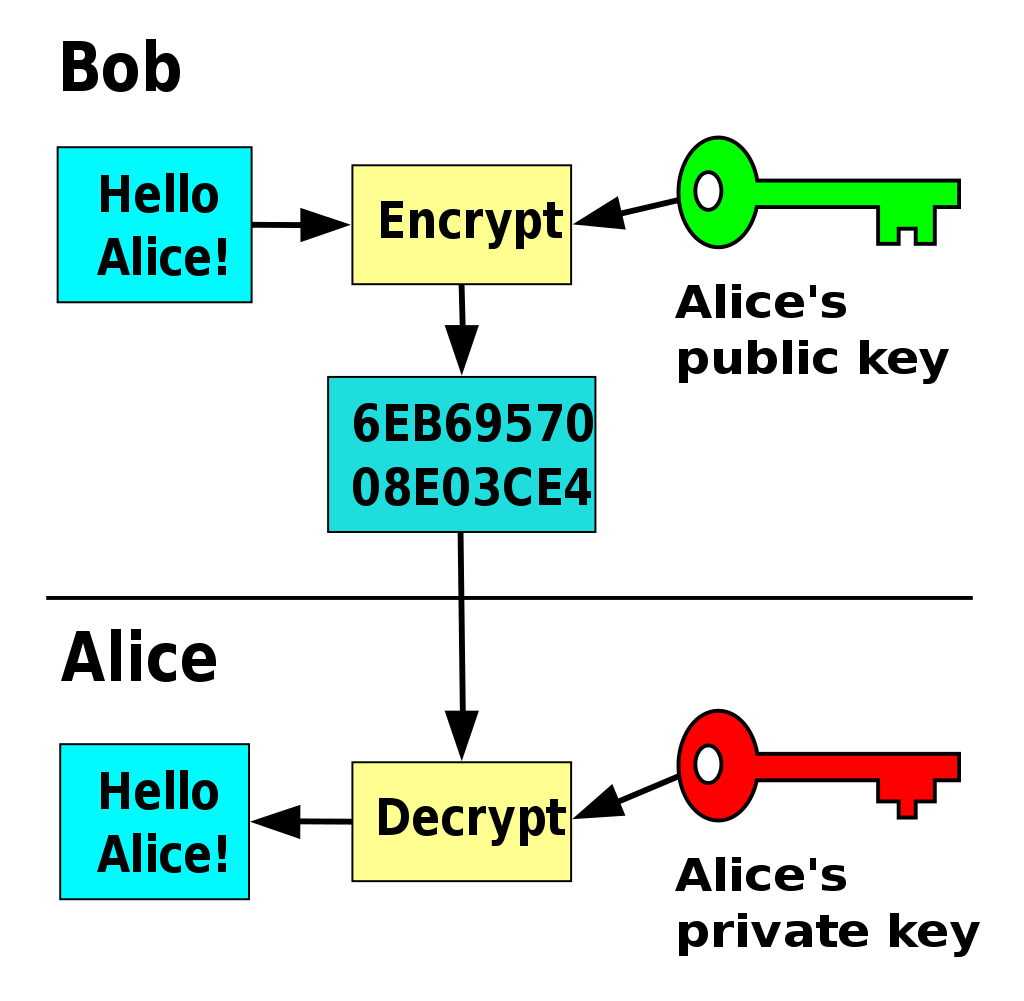
Comparing SSH Keys RSA DSA ECDSA Or EdDSA