Most Secure Hashing Algorithms Are Used To Perform
Most Secure Hashing Algorithms Are Used To Perform - Keeping kids interested can be tough, especially on hectic schedules. Having a stash of printable worksheets on hand makes it easier to provide educational fun without extra prep or electronics.
Explore a Variety of Most Secure Hashing Algorithms Are Used To Perform
Whether you're doing a quick lesson or just want an activity break, free printable worksheets are a great tool. They cover everything from numbers and reading to games and coloring pages for all ages.

Most Secure Hashing Algorithms Are Used To Perform
Most worksheets are quick to print and use right away. You don’t need any special supplies—just a printer and a few minutes to get started. It’s simple, quick, and effective.
With new themes added all the time, you can always find something fresh to try. Just grab your favorite worksheets and turn learning into fun without the stress.

SHA Secure Hashing Algorithm SHA 256 SHA BlockChain Web3
Python most recent call last last 然后点击Source Files下面的Add...,选中你写好的UDF文件,再点击Build进行编译,编译没有错误后,再点击Load,一般会成功。 如果还是出错,可能是其他原因。 1 vs和fluent环境木有配 …

Hashing What It Is How It s Used And Why It Matters With MD5 And
Most Secure Hashing Algorithms Are Used To PerformGabung dan ikuti diskusi perkembangan pasar modal bersama komunitas investor dan trader Mandiri Sekuritas Most most of most most
Gallery for Most Secure Hashing Algorithms Are Used To Perform

Sipher
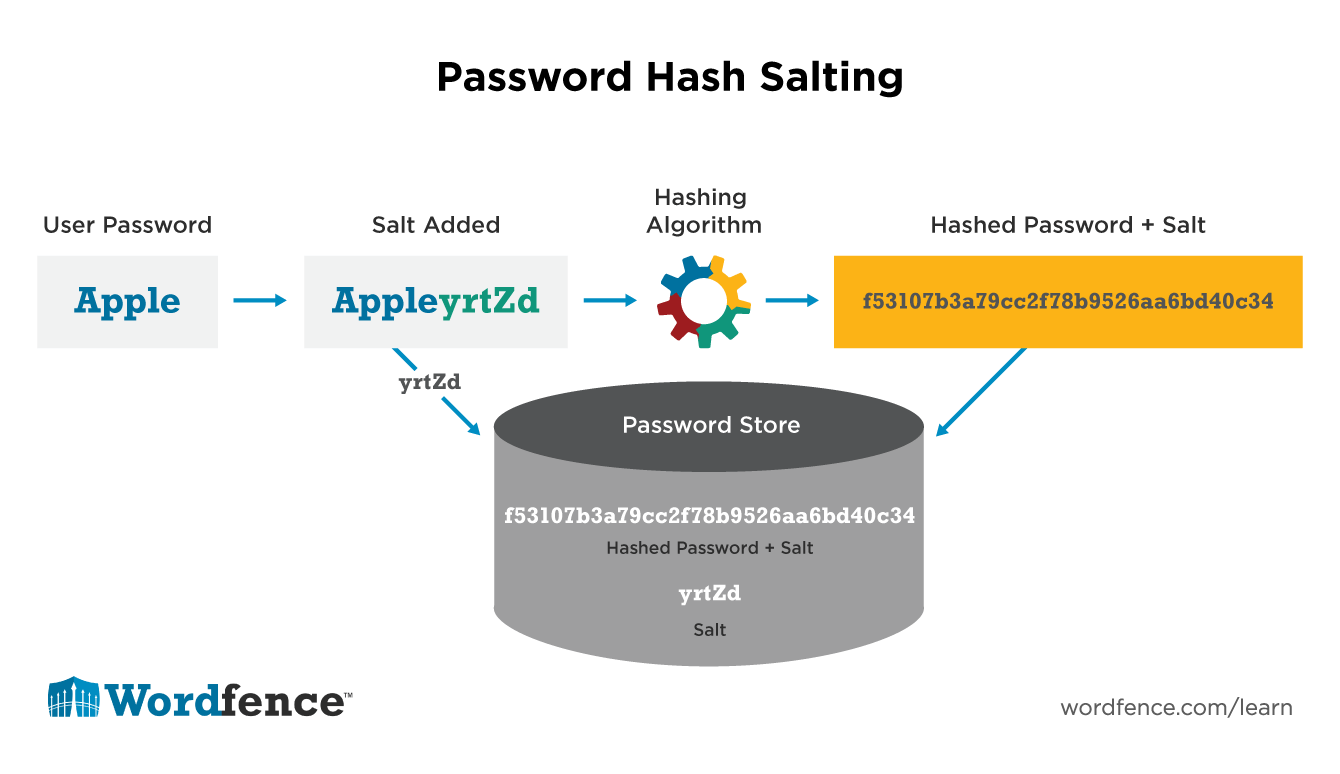
Cyber Security
:max_bytes(150000):strip_icc()/algorithm-df9b57e8ea7c494b891da25987643fab.jpg)
Dukgukim

Hashing Algorithm Overview Types Methodologies Usage Okta
Unsupervised Learning

What Is A Hash Hacking Tutorials By Xeus
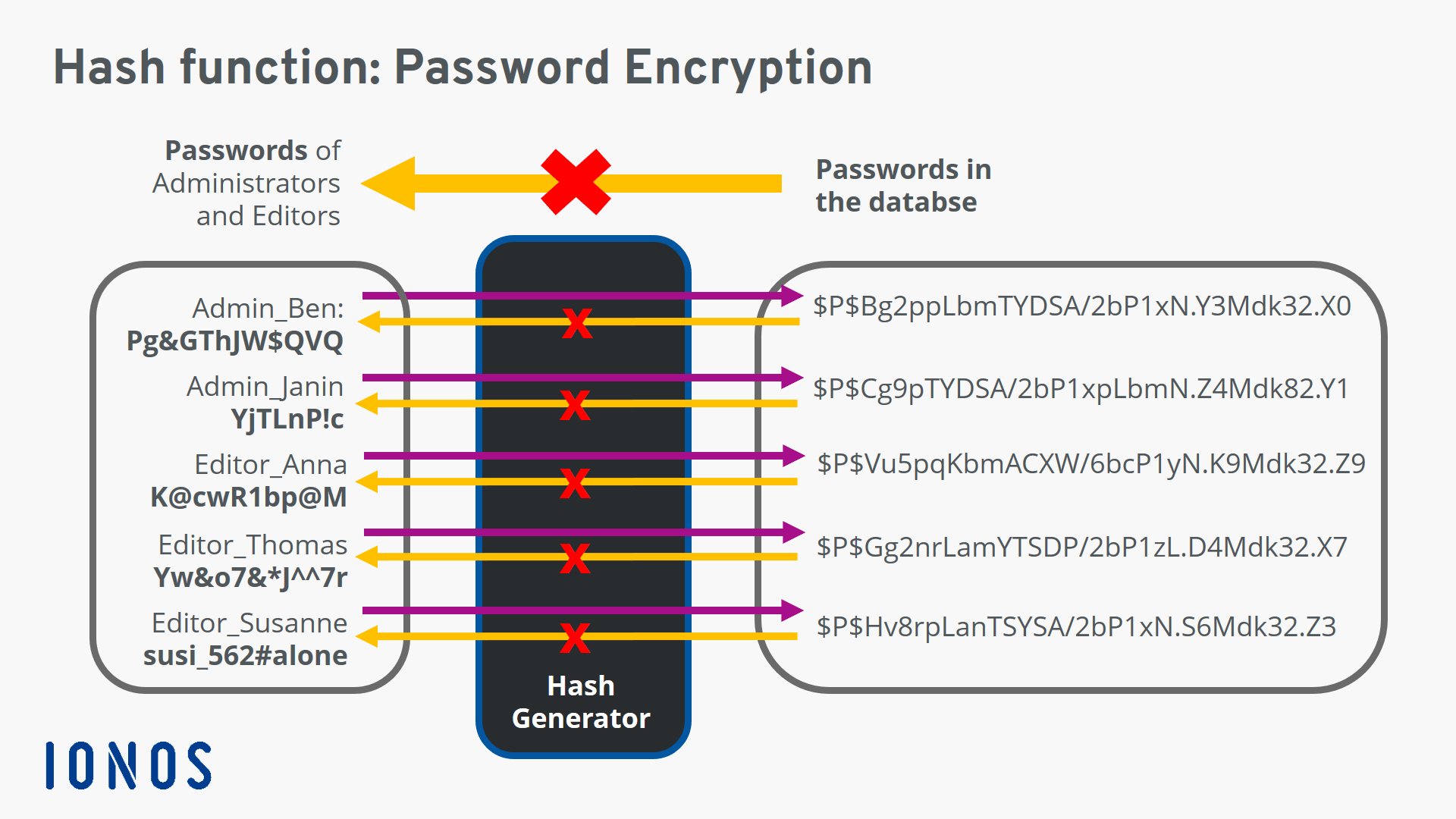
Hash Function Cybersecurity Glossary Vrogue co

Hash Function Cybersecurity Glossary Vrogue co
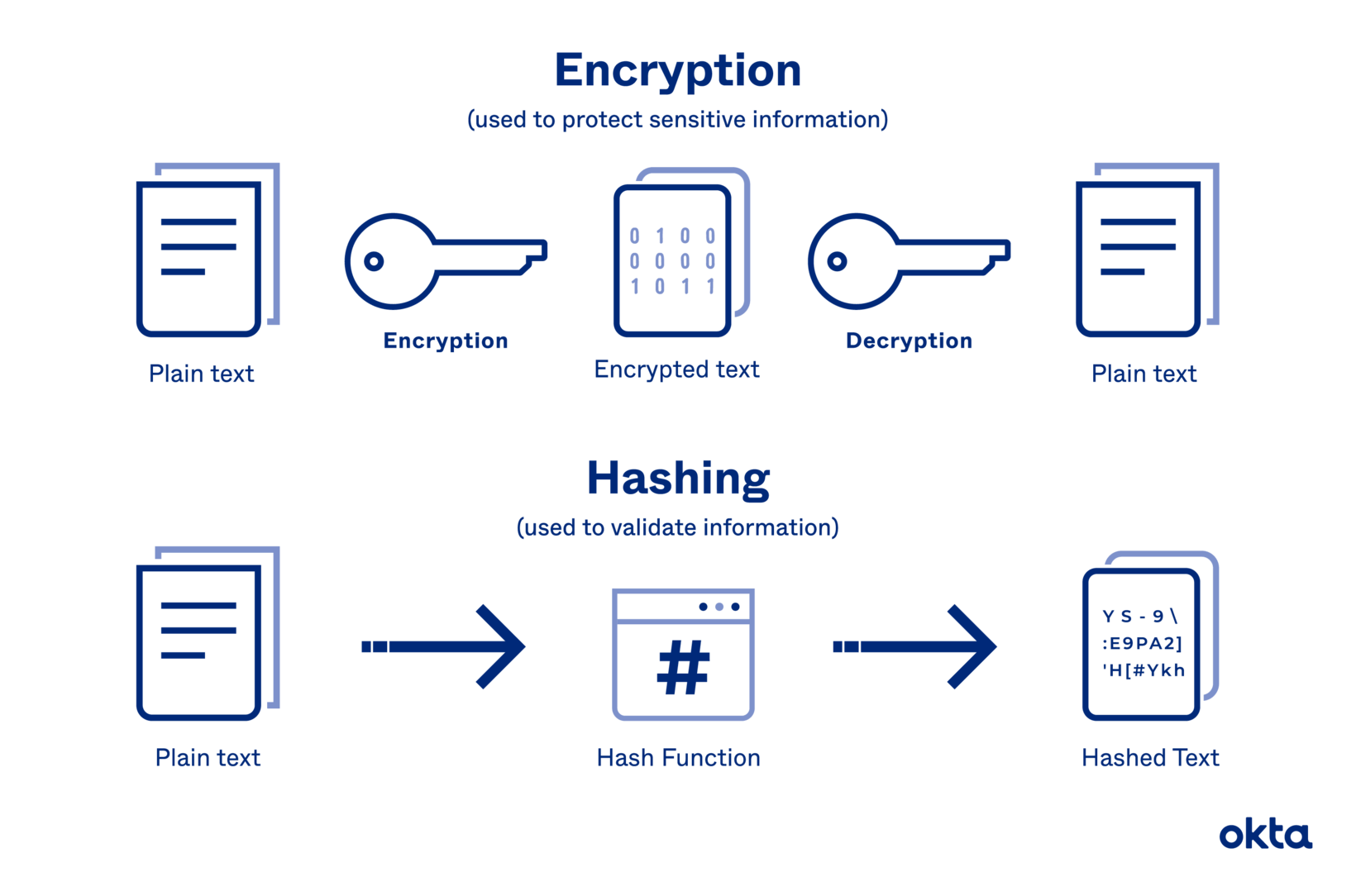
Crittografia PNG Trasparente PNG All
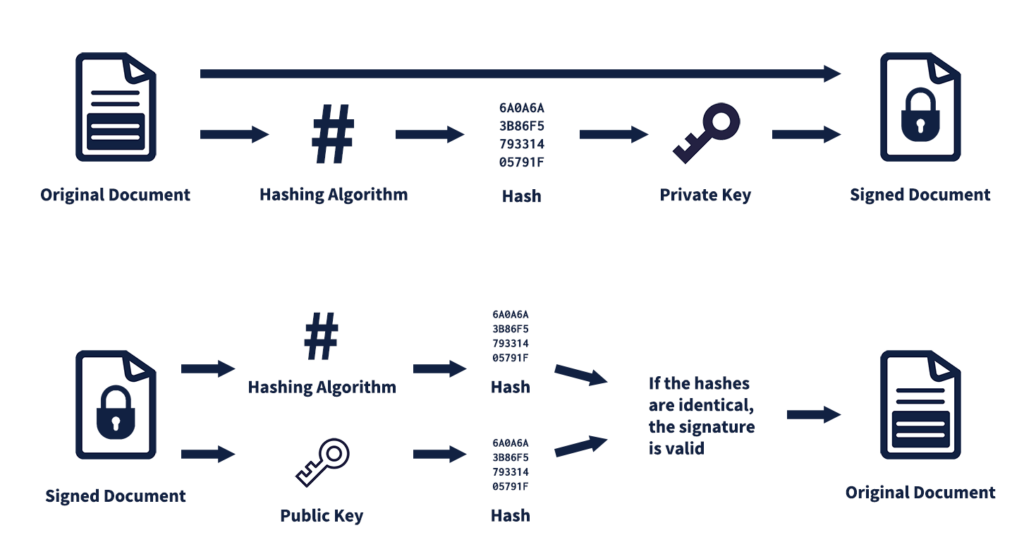
Our Expert Guide To Digital Signature Validation Best Practices