Known Exploited Vulnerabilities Definition
Known Exploited Vulnerabilities Definition - Keeping kids engaged can be challenging, especially on hectic schedules. Having a collection of printable worksheets on hand makes it easier to encourage learning without extra prep or screen time.
Explore a Variety of Known Exploited Vulnerabilities Definition
Whether you're helping with homework or just want an activity break, free printable worksheets are a great tool. They cover everything from numbers and spelling to games and creative tasks for all ages.

Known Exploited Vulnerabilities Definition
Most worksheets are quick to print and use right away. You don’t need any fancy tools—just a printer and a few minutes to get started. It’s simple, fast, and effective.
With new themes added all the time, you can always find something fresh to try. Just grab your favorite worksheets and make learning enjoyable without the stress.
Known Exploited Vulnerabilities Catalog VulnCheck
Dec 11 2023 nbsp 0183 32 In its conclusions and recommendations the Committee says the Home Office must not conflate immigration with human trafficking and modern slavery at the expense of Modern slavery and human trafficking are crimes. Contact the police if you or someone you know is in immediate danger or a victim of human trafficking or modern slavery.

NVD Home
Known Exploited Vulnerabilities DefinitionIt looks likely that the number of victims of modern slavery globally will continue to rise over the coming years. It is vital that we educate potential victims about the risks, how to avoid... We offer digital advice to help people understand whether they or someone they know may have been a victim of human trafficking signpost them to specialist support organisations and
Gallery for Known Exploited Vulnerabilities Definition

CISA Known Exploited Vulnerabilities What To Know VMiss
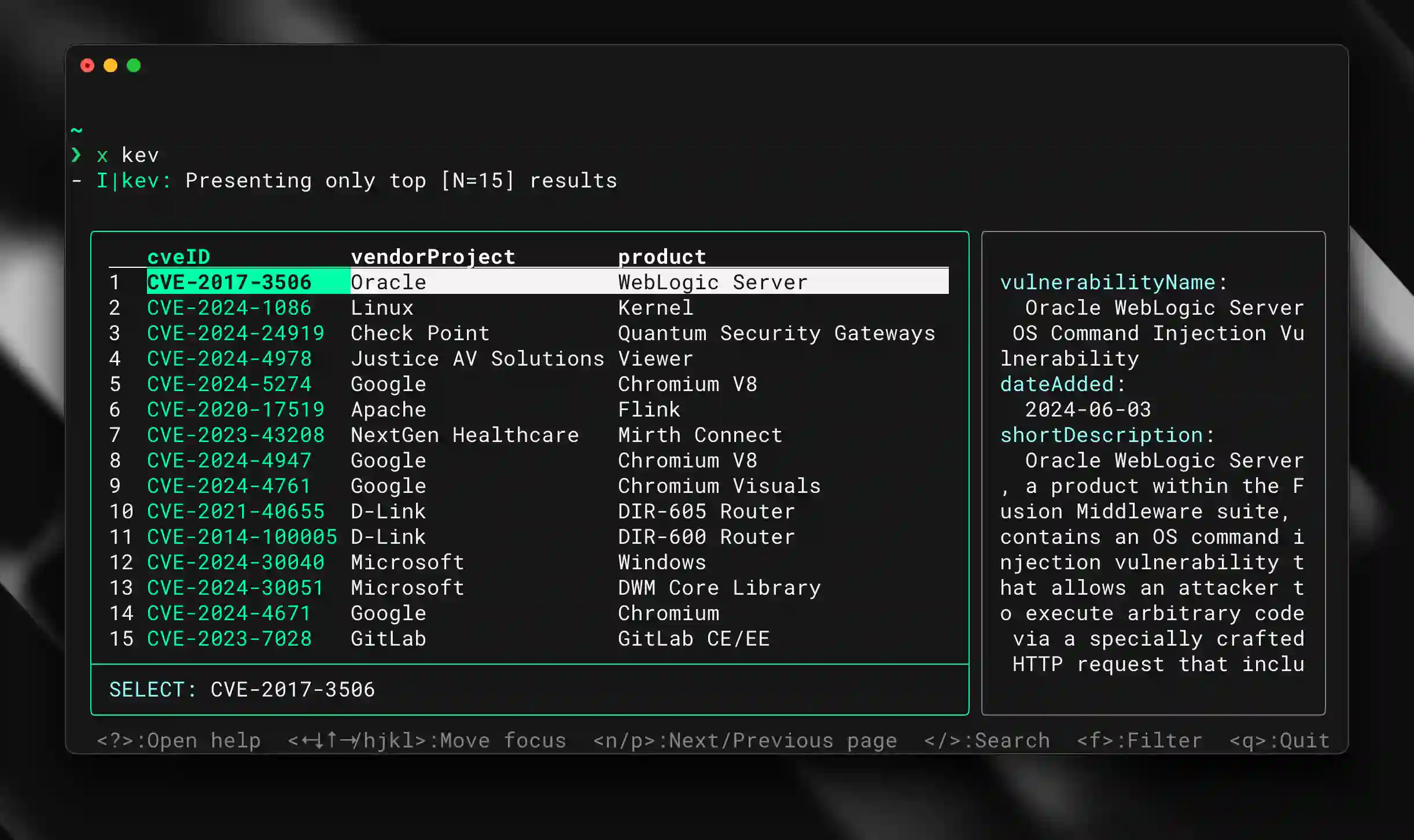
X Kev X cmd Mod KEV Catalog Known Exploited Vulnerabilities
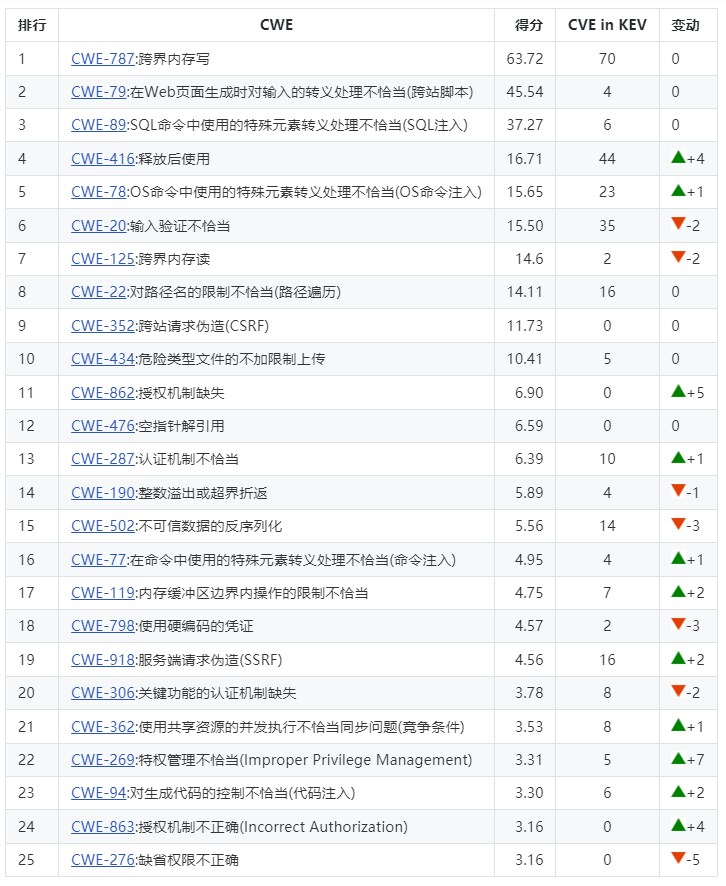
2023 25 CWE TOP 25

Ransomware In 2024 What CISOs Must Know SC Media
What Are Known Exploited Vulnerabilities XM Cyber

How Does The Idea Of Vulnerabilty Debelop Over Tiem Clearance

Zero Day Vulnerabilities CyberHoot

Network Layer Model

Prioritizing CISA Known Exploited Vulnerabilities Blog VulnCheck

Cybernews 2023 KER