Examples Of Hashing Algorithms
Examples Of Hashing Algorithms - Keeping kids occupied can be challenging, especially on busy days. Having a stash of printable worksheets on hand makes it easier to encourage learning without extra prep or electronics.
Explore a Variety of Examples Of Hashing Algorithms
Whether you're supplementing schoolwork or just want an educational diversion, free printable worksheets are a helpful resource. They cover everything from numbers and reading to games and creative tasks for all ages.

Examples Of Hashing Algorithms
Most worksheets are easy to access and use right away. You don’t need any fancy tools—just a printer and a few minutes to set things up. It’s simple, quick, and effective.
With new designs added all the time, you can always find something fresh to try. Just grab your favorite worksheets and make learning enjoyable without the hassle.
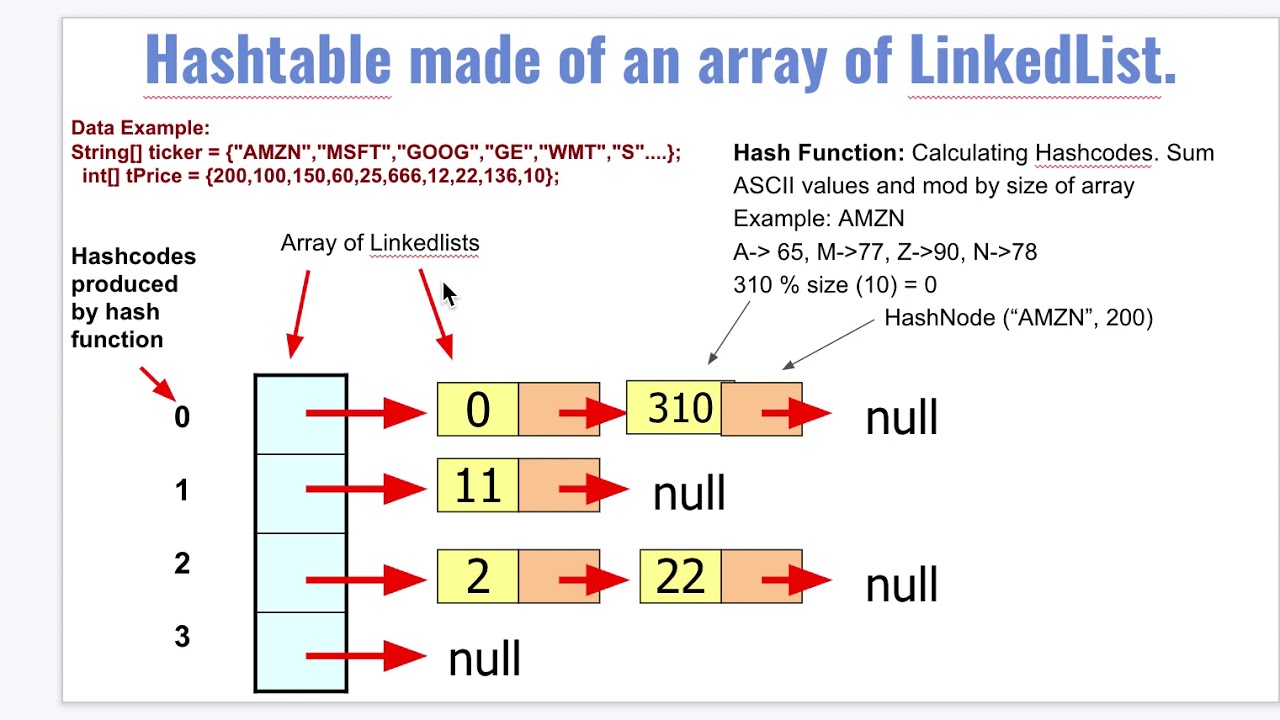
Hash Tables Explained In Simple Terms YouTube
Examples of example in a Sentence Noun He set a good example for the rest of us She gave several examples to show that the program is effective We ve chosen three examples of Example Sentences Examples have not been reviewed. Businesses where hosepipe use is part of their purpose - for example, garden centres and car washes.

Hashing Hashing Algorithms And Collisions Cryptography Practical
Examples Of Hashing AlgorithmsExample definition: one of a number of things, or a part of something, taken to show the character of the whole.. See examples of EXAMPLE used in a sentence. This church is a perfect example of medieval architecture She it and who are all examples of pronouns An early example of privatization was the enclosure of public land for private use by
Gallery for Examples Of Hashing Algorithms

Python Hash Function A Simple Guide With Example YouTube

INTRODUCTION TO HASHING HASHING TYPES OF HASHING EXAMPLES OF

Password Hashing In Node js With Bcrypt YouTube
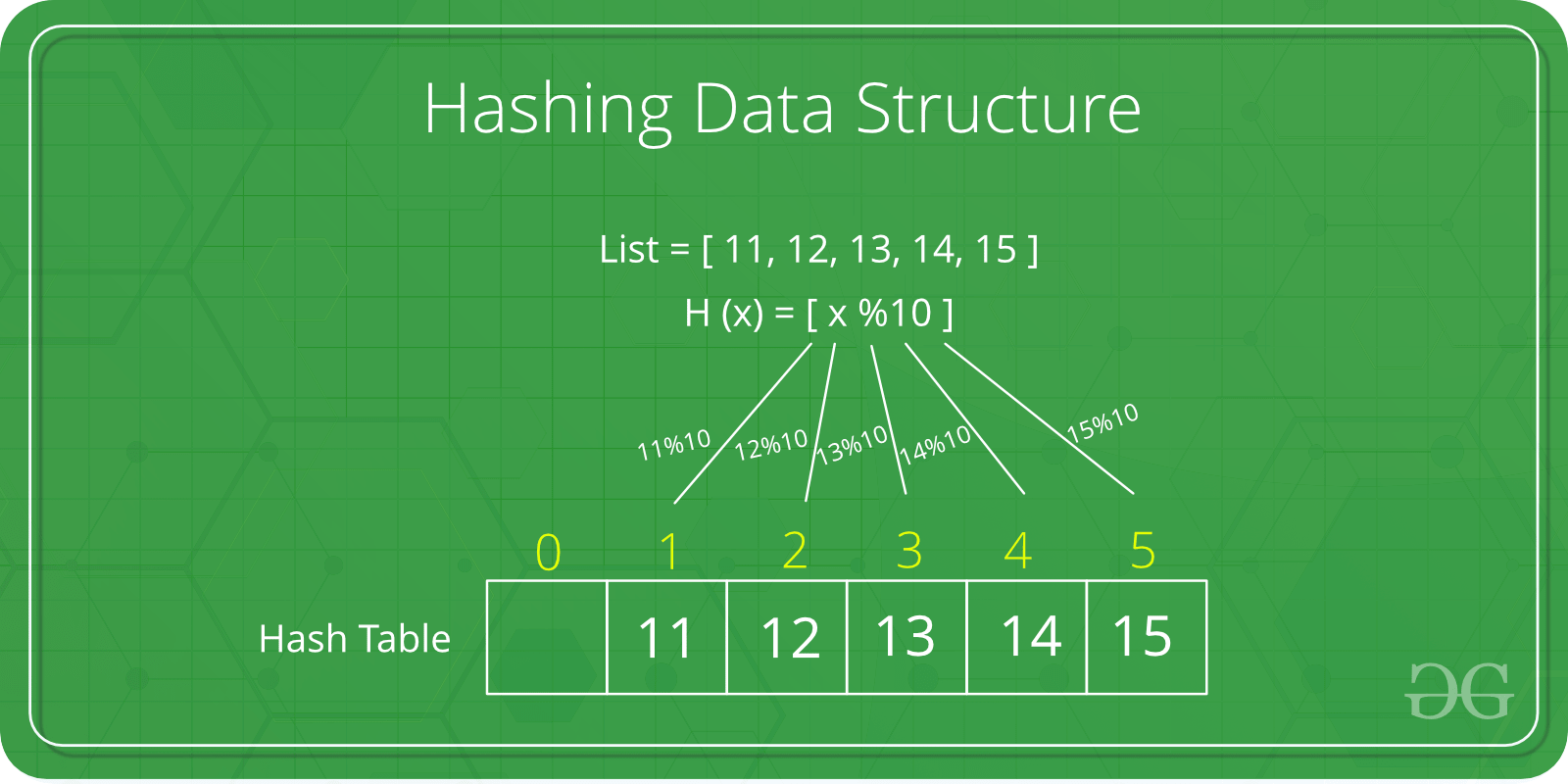
Awesome coding js

GitHub DarshAsawa Cryptography Implementing Various Cipher

Lesson Objectives Aims You Should Know About 1 3 1 Ppt Download

Encryption And Decryption Jean s Blog
Encryption Hashing
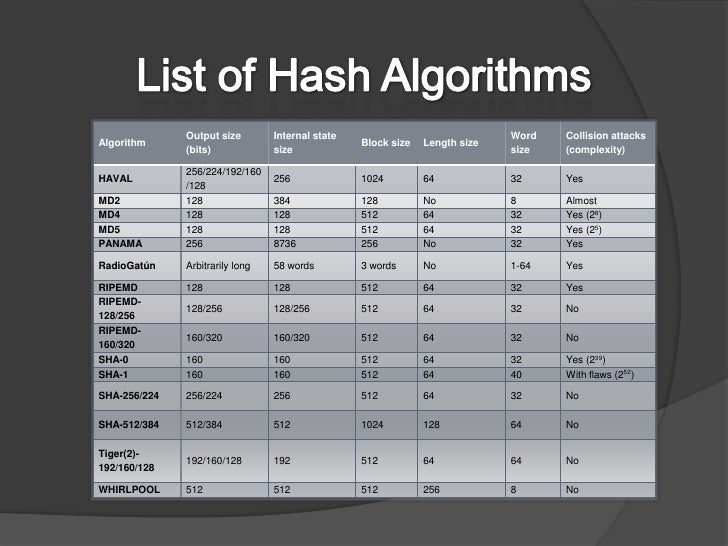
Cryptography Ashik

Hash Function Cybersecurity Glossary Vrogue co