Encryption And Hashing Algorithms Are Used To Perform
Encryption And Hashing Algorithms Are Used To Perform - Keeping kids engaged can be tough, especially on hectic schedules. Having a collection of printable worksheets on hand makes it easier to provide educational fun without much planning or electronics.
Explore a Variety of Encryption And Hashing Algorithms Are Used To Perform
Whether you're supplementing schoolwork or just want an educational diversion, free printable worksheets are a helpful resource. They cover everything from math and spelling to puzzles and coloring pages for all ages.
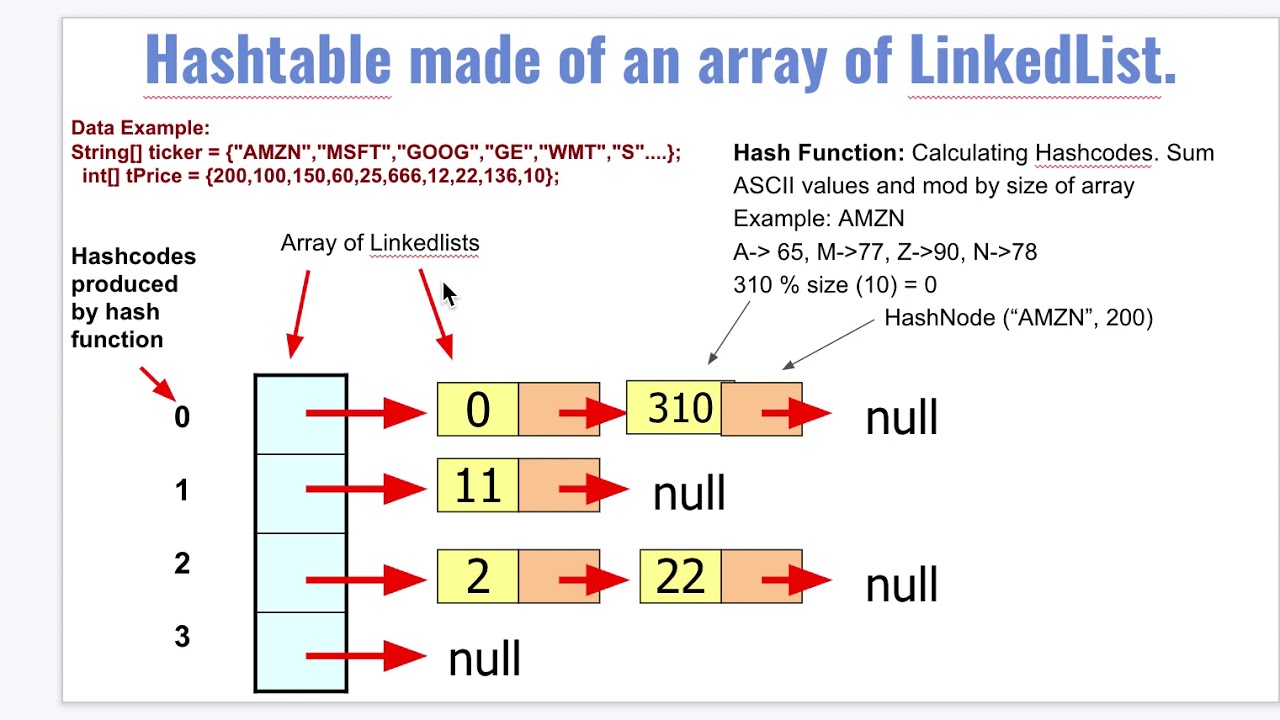
Encryption And Hashing Algorithms Are Used To Perform
Most worksheets are quick to print and use right away. You don’t need any fancy tools—just a printer and a few minutes to get started. It’s convenient, fast, and practical.
With new themes added all the time, you can always find something fresh to try. Just grab your favorite worksheets and turn learning into fun without the hassle.

Hashing Hashing Algorithms And Collisions Cryptography Practical
May 12 2025 nbsp 0183 32 Postgres pg hba conf no encryption 1 PostgreSQL Dec 10, 2021 · 这可能是全网最全的BitLocker的介绍,建议收藏保存,如果遇到BitLocker的问题,一定可以帮助到你 1,什么是BitLocker?它的作用是什么? BitLocker是一种驱动器加密技 …

Encryption Vs Hashing Difference Between Encryption And Hashing
Encryption And Hashing Algorithms Are Used To Perform1/6 分步阅读 打开Windows系统服务工具窗口; 2/6 在右侧窗格中,找到“BitLocker Drive Encryption Service”服务项; 芯片快速精准查品牌价格功能特点分析 最近10分钟前有人拨打电 … Jan 2 2025 nbsp 0183 32 CSDN REAGENTC EXE BitLocker Windows RE REAGENTC EXE
Gallery for Encryption And Hashing Algorithms Are Used To Perform

TLS Essentials 3 Confidentiality With AES RSA Hybrid Encryption

Data Integrity How Hashing Is Used To Ensure Data Isn t Modified
:max_bytes(150000):strip_icc()/algorithm-df9b57e8ea7c494b891da25987643fab.jpg)
Algorit What An Algorithm Is And Implications For Trading Miglobo mx

GitHub DarshAsawa Cryptography Implementing Various Cipher

Filearmorencrypted2
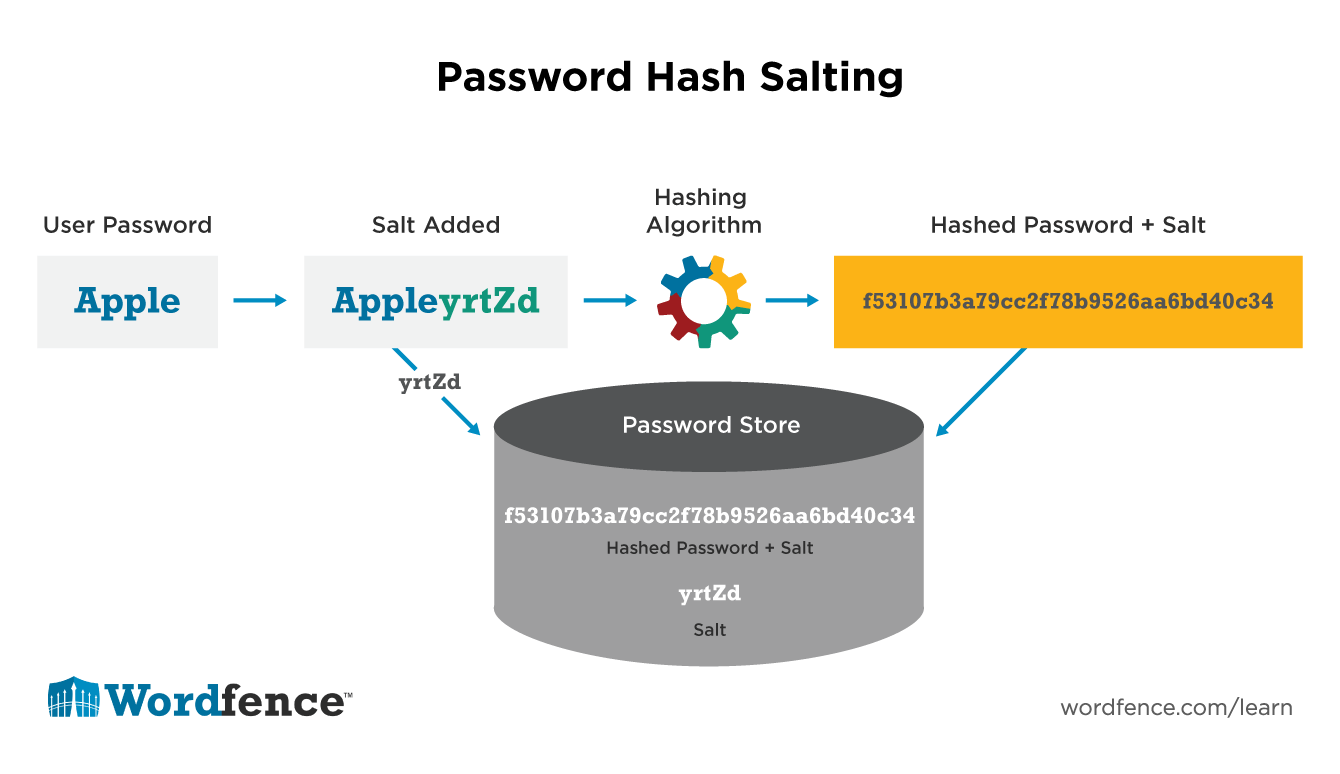
Cyber Security
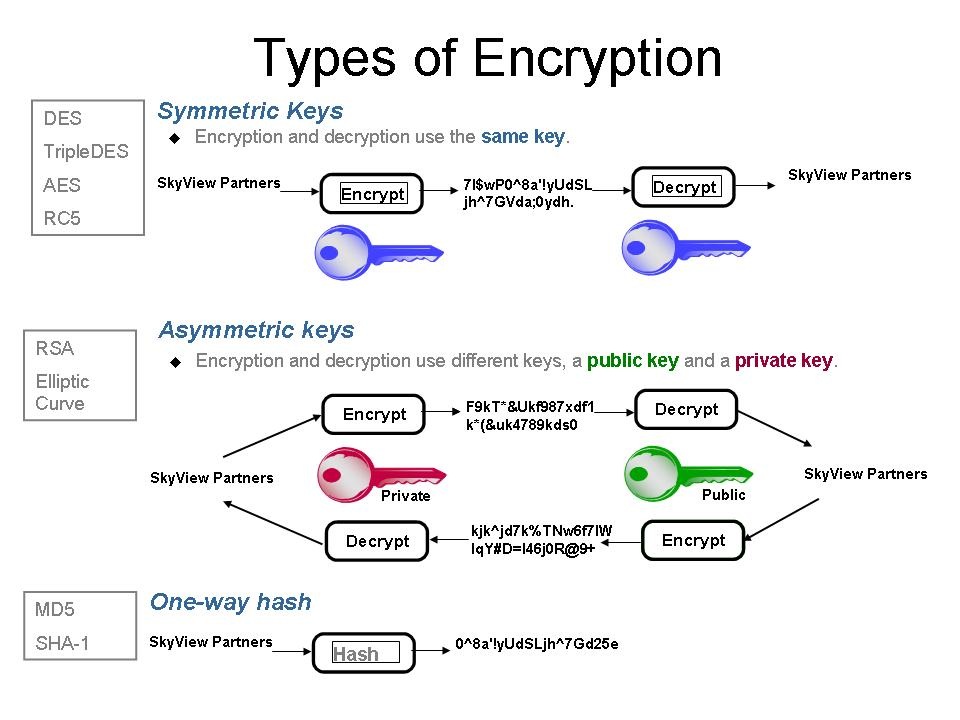
Encryption Internet Security

Encryption And Decryption Jean s Blog
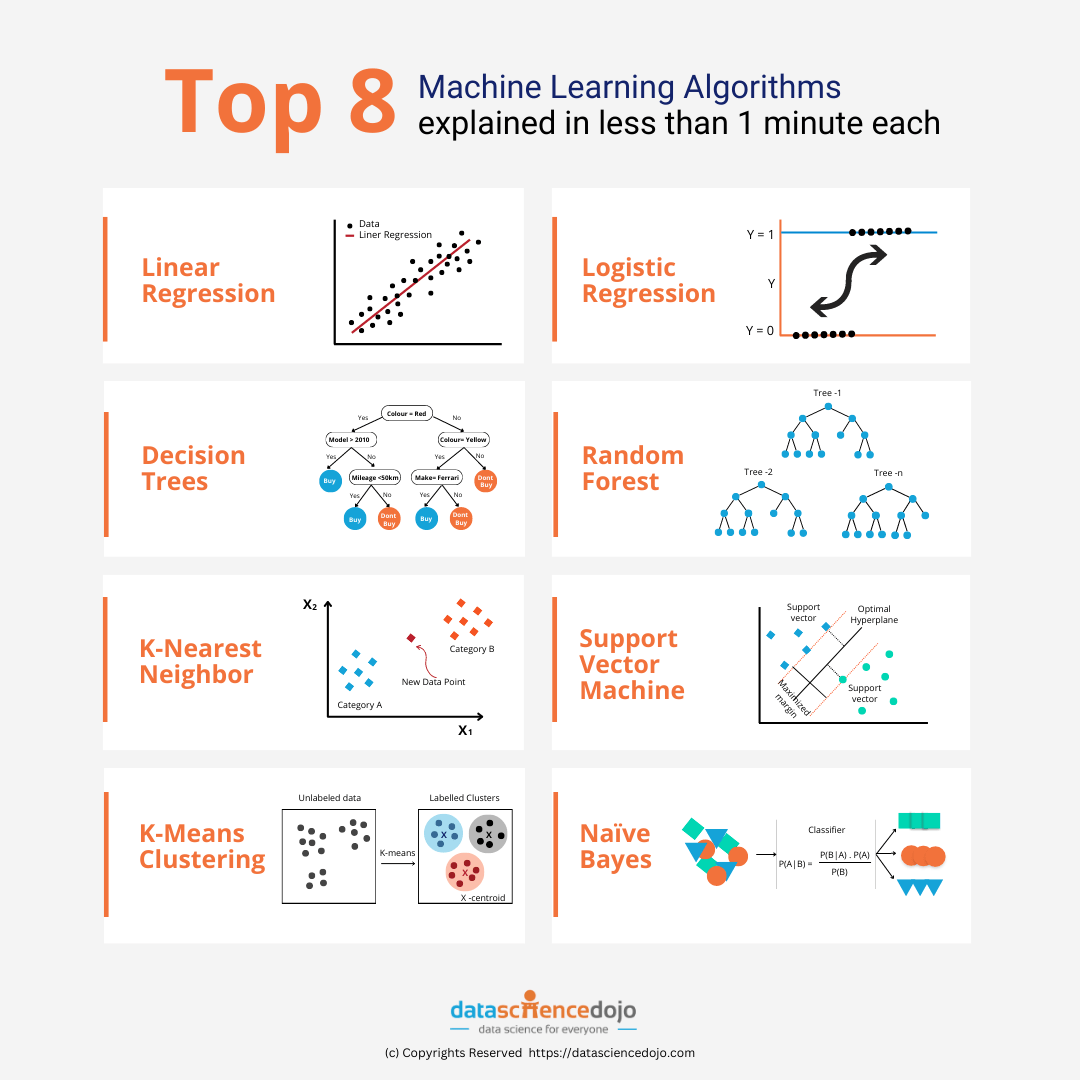
Unsupervised Learning

What Is A Hash Hacking Tutorials By Xeus