Buffer Overflow In Cyber Security
Buffer Overflow In Cyber Security - Keeping kids interested can be tough, especially on busy days. Having a stash of printable worksheets on hand makes it easier to provide educational fun without much planning or electronics.
Explore a Variety of Buffer Overflow In Cyber Security
Whether you're supplementing schoolwork or just want an educational diversion, free printable worksheets are a helpful resource. They cover everything from numbers and spelling to games and coloring pages for all ages.
Buffer Overflow In Cyber Security
Most worksheets are easy to access and use right away. You don’t need any special supplies—just a printer and a few minutes to get started. It’s simple, fast, and practical.
With new designs added all the time, you can always find something exciting to try. Just download your favorite worksheets and turn learning into fun without the hassle.

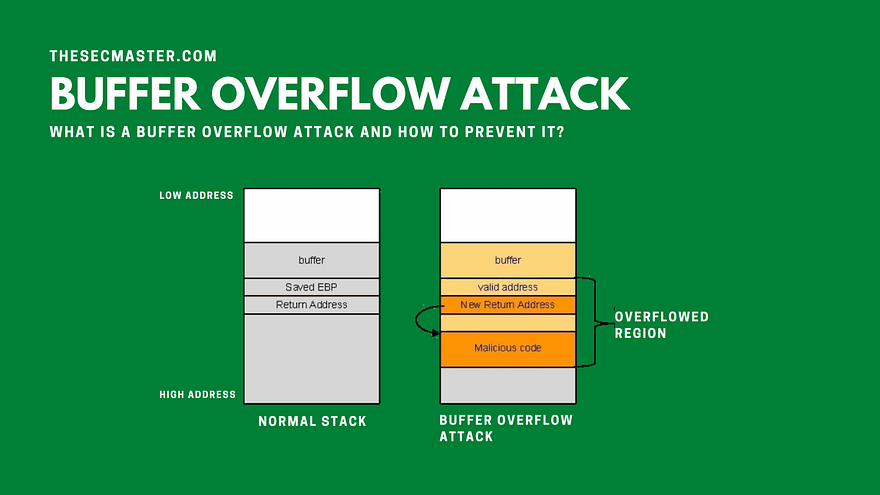
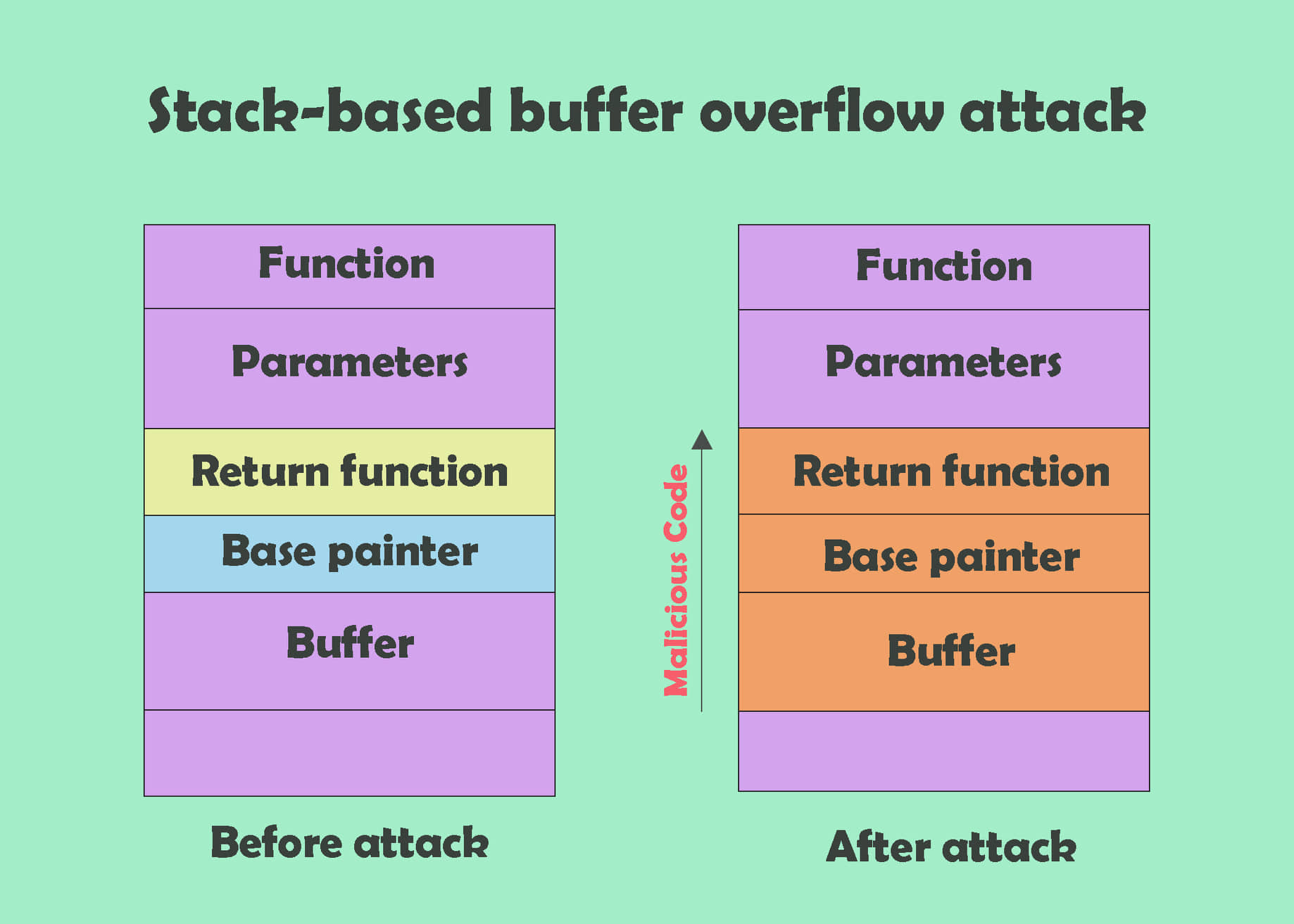
What Is A Buffer Overflow Attack Types Examples
Despite being well understood buffer overflow attacks are still a major security problem that torment cyber security teams In 2014 a threat known as heartbleed exposed hundreds of millions of users to attack because of a buffer overflow vulnerability in SSL software How do attackers exploit buffer overflows Description. Buffer overflow is probably the best known form of software security vulnerability. Most software developers know what a buffer overflow vulnerability is, but buffer overflow attacks against both legacy and.
What Is A Buffer Overflow Attack And How To Prevent It
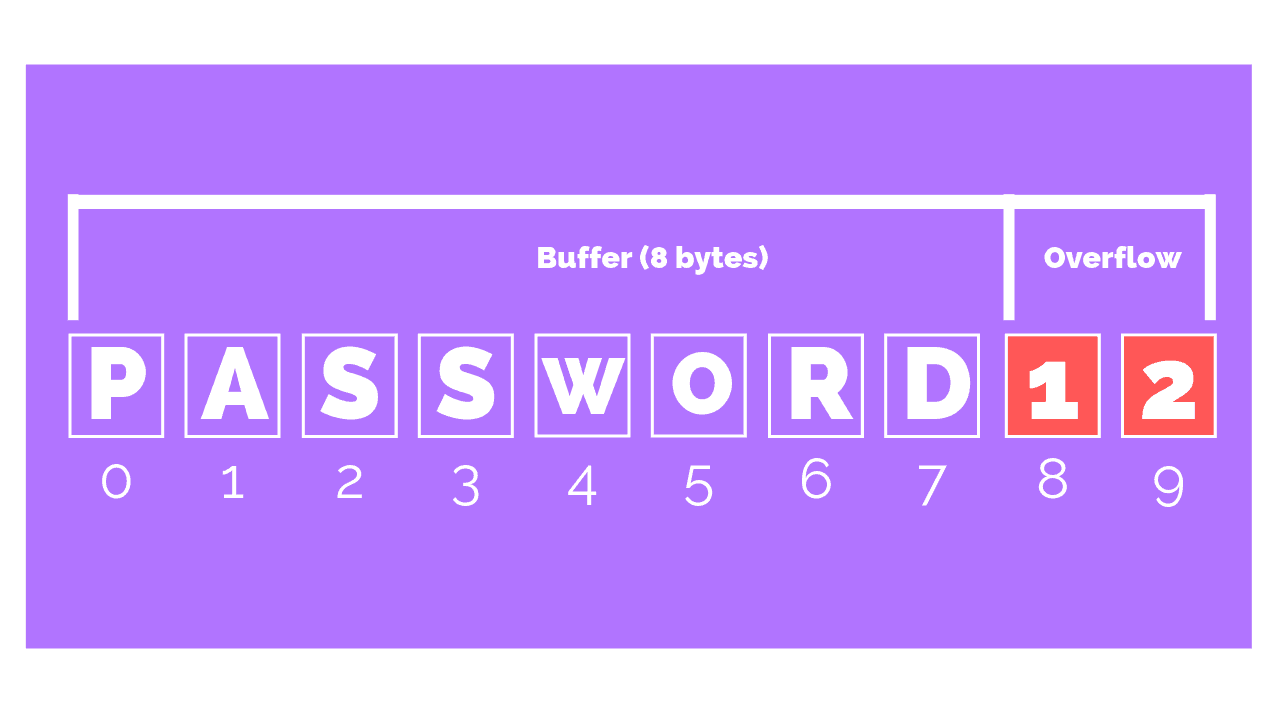
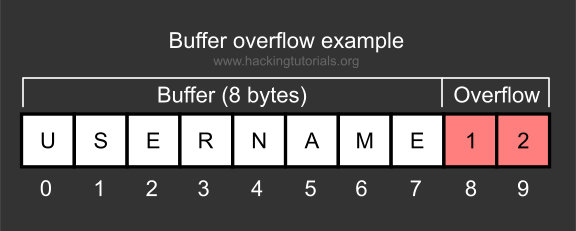
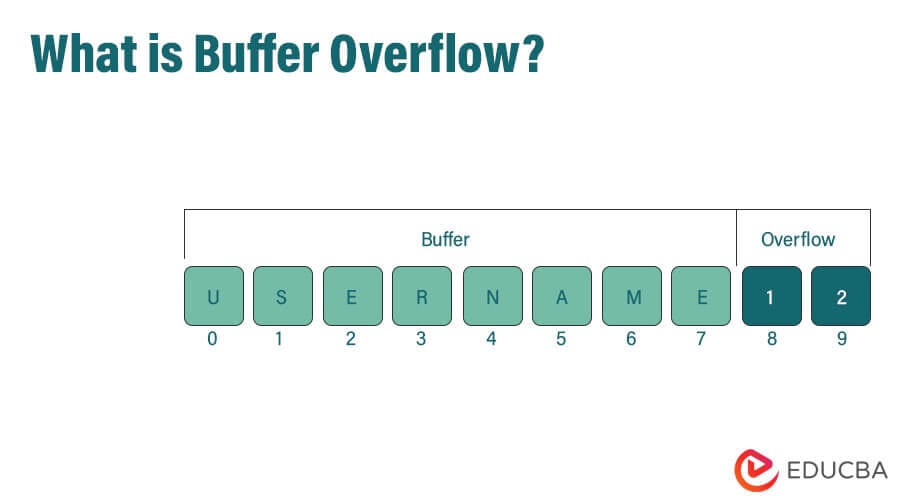
Buffer Overflow In Cyber SecurityA buffer overflow attack is a type of cybersecurity threat that occurs when a program or application tries to store more data in a buffer (temporary storage) than it can actually hold. This excess data can overflow into adjacent memory locations, potentially overwriting important information or causing the program to crash. What is a Buffer Overflow Attack Attackers exploit buffer overflow issues by overwriting the memory of an application This changes the execution path of the program triggering a response that damages files or exposes private information
Gallery for Buffer Overflow In Cyber Security
Buffer Overflow Explained The Basics Penetration Test Resource Page
Top More Than 156 Euphoria Anime Total Episodes Super Hot

N Qu Es Un Desbordamiento De B fer C mo Funcionan Estos Tipos De
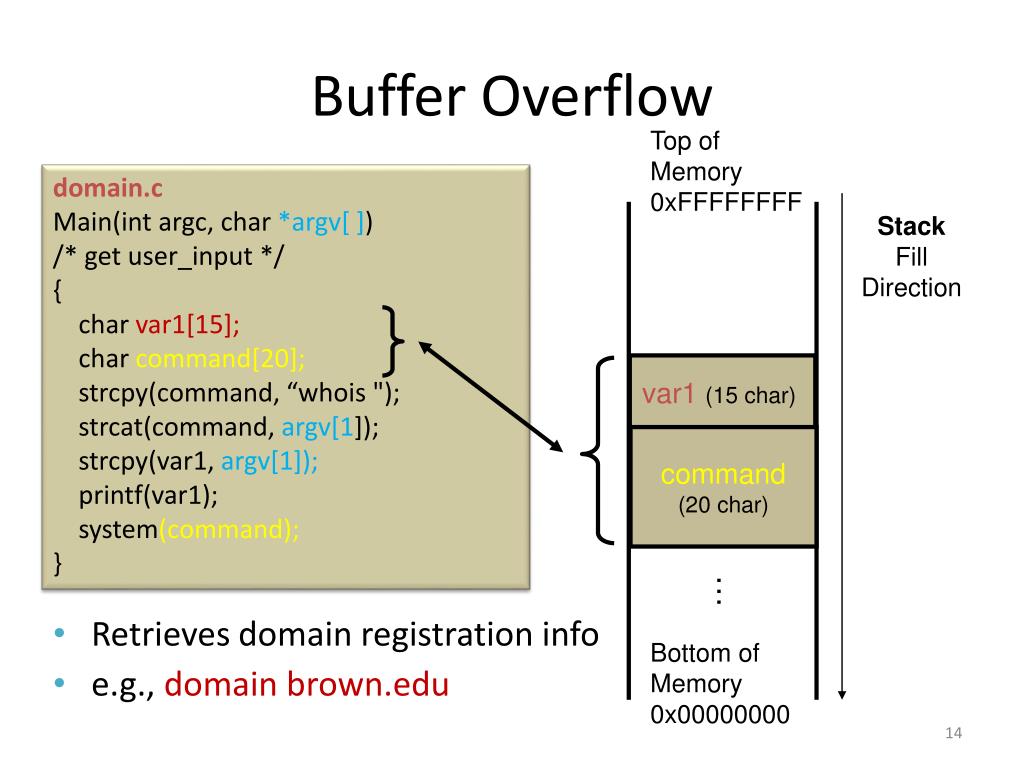
PPT Chapter 3 4 Buffer Overflow Attacks PowerPoint Presentation
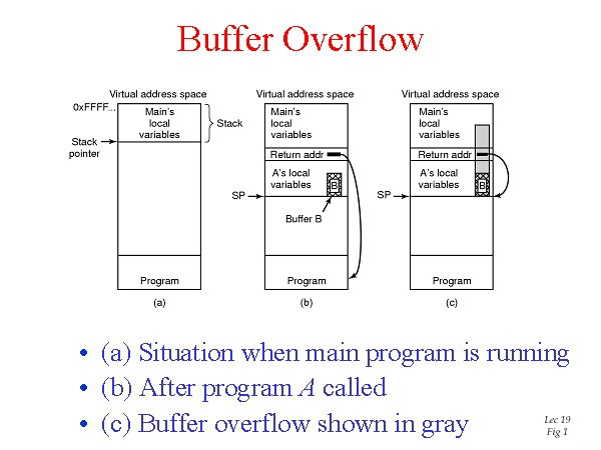
Buffer Overflow K 12 Cybersecurity Educations
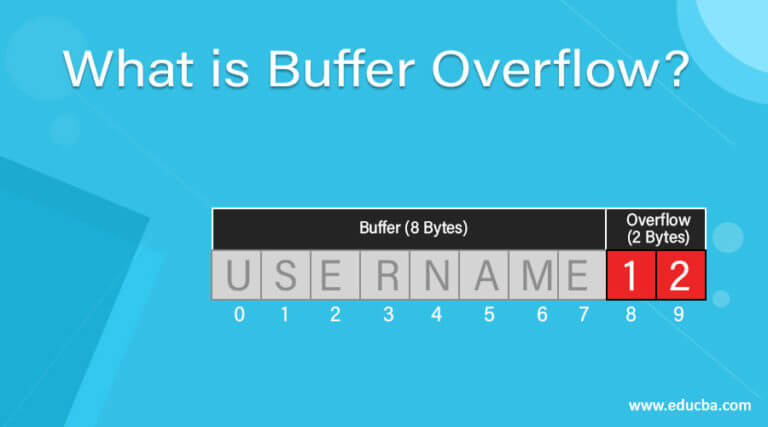
Upload A File To Commit A Buffer Overflow Attack Knight Jece1939

Buffer Overflow Attack Tutorial 0x00 YouTube

Introduction Of Buffer Overflow Cyber Security Notes
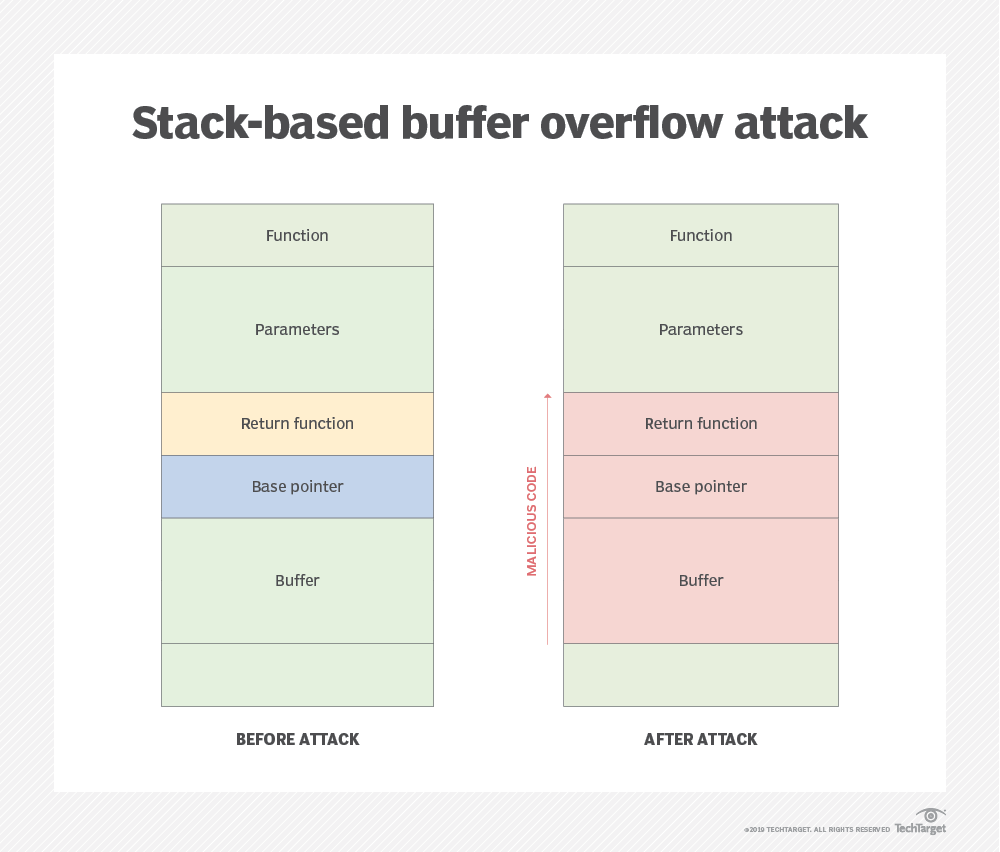
5 Application Security Threats And How To Prevent Them TechTarget
Buffer Overflow Attacks Bir Hosting